「設定に再起動が必要なコンフィグまとめ」の版間の差分
ナビゲーションに移動
検索に移動
ページの作成:「== Cisco == === ISR4000 / ASR1000 === license boot level <License_Level> <ref>Chapter: License Verification <nowiki>https://www.cisco.com/c/en/us/td/docs/routers/asr100…」 |
|||
| (同じ利用者による、間の48版が非表示) | |||
| 1行目: | 1行目: | ||
いろいろなメーカーのネットワーク機器について、再起動しないと有効にならないコンフィグを集めました。 | |||
以下のようなシチュエーションで役に立ちます。 | |||
* 作業の役務を見積もるとき、夜間作業が必要か調べたい | |||
* 保守交換後、OS Ver と running-config で diff が無くても、動作に差分があるとき | |||
** TCAM サイズを変更するコマンドは、ROMMON / Boot Loader の変数に書き込まれて running-config に表示されない機器があります | |||
* 初期構築時に設定追加・変更しておくことで運用に入ってからの停止作業を回避 | |||
== Cisco == | == Cisco == | ||
=== ISR4000 / ASR1000 === | === ISR4000 / ASR1000 === | ||
< | ==== ASR1000 : license boot level { adventerprise | advipservices | ipbase } <ref>Chapter: License Verification | ||
https://www.cisco.com/c/en/us/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG/b_ASR1001HX-1002HX_HIG_chapter_0110.html | |||
license boot level <License_Level></ref> ==== | |||
* Universal イメージの IOS / IOS-XE はコマンドでライセンス レベルを変更可能 | |||
==== ISR4000 : platform hardware throughput level { 2500000 | 5000000 } <ref>Performance | |||
https://www.cisco.com/c/en/us/td/docs/routers/access/4400/software/configuration/guide/isr4400swcfg/bm_isr_4400_sw_config_guide_chapter_0101.html#concept_3F15D3B0CBA64CA9BADC3C84FE0C63FB | |||
To configure the throughput level, perform the following steps and to upgrade the throughput level use the platform hardware throughput level { 2500000 | 5000000} command. | |||
In the user EXEC configuration mode, enter the enable command. | |||
Enter configure terminal command to enter the global configuration mode. | |||
To upgrade the throughput level, enter the platform hardware throughput level{2500000|5000000} command. | |||
To exit global configuration mode, enter exit. | |||
To save the configuration, enter the copy running-config startup-config command. | |||
To reload the router enter reload. '''A reload is required to activate the throughput level.'''</ref> ==== | |||
==== ISR4000 : platform hardware throughput level boost <ref>platform hardware throughput level boost | |||
https://www.cisco.com/c/en/us/td/docs/routers/access/4400/software/configuration/guide/isr4400swcfg/bm_isr_4400_sw_config_guide_chapter_0101.html#concept_x2p_pkj_ndb | |||
< | Save the configuration and reload the device to enable Boost performance license. '''After the reload,''' the Boost Performance is activated as shown in this example.</ref>==== | ||
==== ASR1000 : platform hardware throughput level <ref>スループット レベルの設定 | |||
https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001-x/asr1hig-book/asr1hig-book_chapter_0101.html#con_1060881 | |||
Cisco ASR 1001-X ルータの組み込みエンベデッド サービス プロセッサは、ソフトウェア ライセンスに応じて、2.5 Gbps(デフォルト)、5 Gbps、10 Gbps、および 20 Gbps のスループットをサポートします。 | Cisco ASR 1001-X ルータの組み込みエンベデッド サービス プロセッサは、ソフトウェア ライセンスに応じて、2.5 Gbps(デフォルト)、5 Gbps、10 Gbps、および 20 Gbps のスループットをサポートします。 | ||
| 20行目: | 56行目: | ||
コマンドを実行します。 | コマンドを実行します。 | ||
次に、20 Gbps パフォーマンス アップグレード | 次に、20 Gbps パフォーマンス アップグレード ライセンスの適用と'''ルータのリロード後'''の | ||
このコマンドの出力例を示します。</ref>==== | |||
* デフォルトは'''双方向'''で合計 2.5Gbps のスループット | |||
* '''双方向'''で 20Gbps の最大スループットを設定可能 | |||
** 10G ポートの Rx / Tx の合計で 20Gbps を捌けるのと、同一の意味 | |||
* CSR1000V は再起動が不要と記載あり | |||
==== ASR1001-HX : platform hardware crypto-throughput level { 8g | 8-16g } <ref>暗号化スループット レベルの設定<nowiki/>https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG.pdf | |||
Cisco ASR 1001-HX ルータの暗号化スループット レベルを設定するには、次のコマンドを入力します。<syntaxhighlight lang="diff"> | |||
Router(config)# platform hardware crypto-throughput level ? | |||
8-16g crypto throughput upgrade, bits per second | |||
8g crypto throughput level, bits per second | |||
Router(config)# platform hardware crypto-throughput level 8g | |||
% Crypto Bandwidth set to 8G bps. | |||
Router(config)# platform hardware crypto-throughput level 8-16g | |||
% Crypto Bandwidth set to 16G bps. | |||
</syntaxhighlight></ref> ==== | |||
* こちらは再起動が必要無いように読める | |||
==== ASR1002-HX : platform hardware crypto-throughput level { 8g | 8-16g | 8-25g | 16-25g } <ref>暗号化スループット レベルの設定<nowiki/>https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG.pdf | |||
Cisco ASR 1002-HX ルータの暗号化スループット レベルを設定するには、次のコマンドを入力します。<syntaxhighlight lang="diff"> | |||
Router(config)# platform hardware crypto-throughput level ? | |||
16-25g crypto throughput upgrade, bits per second | |||
8-16g crypto throughput upgrade, bits per second | |||
8-25g crypto throughput upgrade, bits per second | |||
8g crypto throughput level, bits per second | |||
</syntaxhighlight></ref> ==== | |||
* こちらは再起動が必要無いように読める | |||
=== Catalyst8200 / 8300 === | |||
==== [https://www.cisco.com/c/en/us/td/docs/routers/cloud_edge/c8300/software_config/cat8300swcfg-xe-17-book/isr9000swcfg-xe-16-12-book_chapter_010.html#concept_0FBABD5F74924D36895FEF9912A283CF platform resource { service-plane-heavy | data-plane-heavy }] ==== | |||
* Catalyst 8200 , 8300 は複数の CPU コアを、サービス プレーンとデータプレーンに振り分ける割合を変えることが可能 | |||
* 最小 8 コアを備えている | |||
* デフォルトは service-plane-heavy | |||
* show platform software cpu alloc コマンドで、割り当て状況を確認可能 | |||
<syntaxhighlight lang="diff"> | |||
show platform software cpu alloc | |||
CPU alloc information: | |||
Control plane cpu alloc: 0 | |||
Data plane cpu alloc: 1-7 | |||
Service plane cpu alloc: 0 | |||
Template used: CLI-data_plane_heavy | |||
</syntaxhighlight> | |||
==== [https://www.cisco.com/c/en/us/td/docs/routers/cloud_edge/c8300/software_config/cat8300swcfg-xe-17-book/m-available-licenses.html#Cisco_Task.dita_3e328700-9d53-4aa0-92d7-39de3006cc7f platform hardware throughput crypto] ==== | |||
=== Catalyst 2960 / 3750 | ==== [https://www.cisco.com/c/en/us/td/docs/routers/cloud_edge/c8300/software_config/cat8300swcfg-xe-17-book/m-available-licenses.html#Cisco_Task.dita_3e328700-9d53-4aa0-92d7-39de3006cc7f platform hardware throughput level MB] ==== | ||
sdm prefer { access | default | dual-ipv4-and-ipv6 { default | routing | vlan } | indirect-ipv4-and-ipv6-routing | routing | vlan } <ref>Chapter: Configuring SDM Templates | |||
==== [https://www.cisco.com/c/en/us/td/docs/routers/cloud_edge/c8300/software_config/cat8300swcfg-xe-17-book/m-available-licenses.html#Cisco_Task.dita_34eb5481-3d5e-431a-9c39-6e19c76d893e (EXEC) license throughput crypto auto-convert] ==== | |||
==== [https://www.cisco.com/c/en/us/td/docs/routers/cloud_edge/c8300/software_config/cat8300swcfg-xe-17-book/m-available-licenses.html#Cisco_Task.dita_34eb5481-3d5e-431a-9c39-6e19c76d893e (EXEC) license throughput level auto-convert] ==== | |||
=== Cisco 8000 === | |||
==== hw-module profile route scale lpm tcam-banks <ref>[https://www.cisco.com/c/en/us/td/docs/iosxr/cisco8000/ip-addresses/b-ip-addresses-cr-8k/m-cisco-express-forwarding-commands.html#wp1459049907 hw-module profile route scale]</ref> ==== | |||
=== Catalyst 2960 / 3560 / 3750 === | |||
==== 3750 : sdm prefer { access | default | dual-ipv4-and-ipv6 { default | routing | vlan } | indirect-ipv4-and-ipv6-routing | routing | vlan } <ref>Chapter: Configuring SDM Templates | |||
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_2_se/configuration/guide/3750x_cg/swsdm.html</ref>==== | |||
* PBR / IPv6 はデフォルトで TCAM が割り当てられていないため、routing / dual stack テンプレートに変更 + 再起動が必要 | |||
==== system mtu jumbo <1500-9000> | <1500-9198> ==== | |||
* show run に出てこない | |||
* show system mtu コマンドで確認可能 | |||
* 機種により対応範囲が異なる | |||
** 3750G : 1500-9000 | |||
** 3560CX : 1500-9198<br /> | |||
=== Catalyst 4500 Sup6E === | |||
==== hw-module uplink mode { shared-backplane| tengigabitethernet } <ref>Supervisor Engine 6-E でのアップリンク モードの選択 | |||
https://www.cisco.com/c/ja_jp/td/docs/sw/lanswt-access/cat4500swt/cg/009/confg-gd/sw-int.html#18105 | |||
(注) hw-module uplink mode shared-backplane コマンドを使用して | |||
アップリンク モードを'''変更する場合は、システムをリロードする必要'''が | |||
あります。コンソールには、リロードを示すメッセージが表示されます。</ref> ==== | |||
* 要再起動 | |||
* 最初に TenGig を使っていなくて、増速で TenGig にするときに要注意 | |||
==== hw-module module <module_num> port-group <port_num> select [ gigabitethernet | tengigabitethernet ] ==== | |||
* WS-X4606-10GE-E で TwinGig コンバーターを使用するときに使用 | |||
* こちらは'''再起動の必要無し''' | |||
=== Catalyst 6500 Sup720 / Sup720-10G === | |||
==== mls cef maximum-routes <ref>CAT 6500 and 7600 Series Routers and Switches TCAM Allocation Adjustment Procedures | |||
https://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/117712-problemsolution-cat6500-00.html#anc3 | |||
You can enter the mls cef maximum-routes ip <number in thousands> command in order to adjust the number of routing entries that are allocated to the IPv4. This does not increase the overall size of the FIB TCAM, but it reduces the number of routing entries that are allocated to the IPv6 in order to increase the amount of TCAM space for the IPv4.</ref>==== | |||
=== Catalyst 6500 / 6800 Sup2T / Sup6T === | |||
==== 共通 : vlan internal allocation policy { ascending | descending } <ref>Configuring the Internal VLAN Allocation Policy<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf | |||
Note | |||
The internal VLAN allocation policy is applied only following a reload. </ref> ==== | |||
==== 共通 : platform hardware acl reserve qos-banks { 1 | 2} <ref>Chapter 23 Restrictions for PFC QoS<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf | |||
Changes to the supported number of '''QoS TCAM entries take effect after a reload'''. Enter the show platform hardware acl | |||
global-config command to display the QoS TCAM entry configuration:</ref> ==== | |||
==== Sup6T : hw-module switch {switch-id} slot {sup slot no.} operation-mode port-group {Port-group no. } { TenGigabitEthernet | FortyGigabitEthernet } <ref name=":0">Chapter 4 Virtual Switching Systems<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf | |||
Note - The entire '''systems reloads after any mode conversion'''.</ref> ==== | |||
==== Sup6T : hw-module switch {switch-id} slot {sup slot no.} performance { TenGigabitEthernet | FortyGigabitEthernet } <ref name=":0" /> ==== | |||
=== Catalyst 3850 / 3650 / 9000 === | === Catalyst 3850 / 3650 / 9000 === | ||
< | ==== license boot level <license_level> <ref>Configuring Base and Add-On Licenses | ||
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/17-6/configuration_guide/sys_mgmt/b_176_sys_mgmt_9300_cg/licenses.html#Cisco_Task.dita_f126c327-a647-4235-b1a2-930771e49f9d | |||
license boot level <license_level></ref> | license boot level <license_level></ref>==== | ||
* Universal イメージの IOS / IOS-XE はコマンドでライセンス レベルを変更可能 | |||
* グローバル コンフィギュレーションで実施 | |||
< | ==== 9000 : license right-to-use [activate <kbd>|</kbd> deactivate ] [network-essentials <kbd>|</kbd> network-advantage ] [all <kbd>|</kbd> evaluation {all <kbd>|</kbd> slot <var>slot-number <1-8></var>}] [acceptEULA] <ref name=":1">[https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/16-6/configuration_guide/sys_mgmt/b_166_sys_mgmt_9300_cg/b_166_sys_mgmt_9300_cg_chapter_011.html#task_gfk_vvj_n1b Activating a License]</ref> ==== | ||
* こちらは EXEC モードで実施 | |||
* Evaluation (評価) モードで動作している場合は、ライセンスを購入して right-to-use で Permanent モードに変更します | |||
* | ==== 9000 : license right-to-use [activate | deactivate ] addon [dna-essentials | dna-advantage ] [all | evaluation | subscription {all | slot slot-number <1-8>}] [ acceptEULA] <ref name=":1" /> ==== | ||
* こちらは EXEC モードで実施 | |||
* Evaluation (評価) モードで動作している場合は、ライセンスを購入して right-to-use で Permanent モードに変更します | |||
==== 9500 : sdm prefer { core <kbd>|</kbd> nat <kbd>|</kbd> distribution <kbd>|</kbd> custom } <ref>Chapter: Configuring SDM Templates | |||
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-6/configuration_guide/sys_mgmt/b_176_sys_mgmt_9500_cg/configuring_sdm_templates.html</ref>==== | |||
* 9500H デフォルトの Core テンプレートの場合は MAC アドレステーブルや ARP が少ないため、Distribution に変更するケースがあります | |||
=== Catalyst 3850XS 16.3.3- / 9400 / 9500 / 9600 === | |||
==== stackwise-virtual -> domain <domain_id> <ref>Configuring Cisco StackWise Virtual Settings | |||
<nowiki>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_lbj_yyx_31b</nowiki> | |||
Step 5 | |||
Device(config)#stackwise-virtual | |||
Step 6 | |||
Device(config-stackwise-virtual)#domain 2 | |||
'''Step 10''' | |||
reload</ref> ==== | |||
==== secure-stackwise-virtual authorization-key <128-bits> <ref>[https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/17-6/configuration_guide/ha/b_176_ha_9600_cg/configuring_cisco_stackwise_virtual.html Configuring Secure StackWise Virtual] | |||
Step 3 | |||
secure-stackwise-virtual authorization-key <128-bits> | |||
Example: | |||
<code>Device(config)#<kbd>'''secure-stackwise-virtual authorization-key <128-bits>'''</kbd></code> | |||
Step 4 | |||
reload | |||
Example: | |||
<code>Device#<kbd>'''reload'''</kbd></code> | |||
</ref> ==== | |||
* 初期設定時のみと思われるため、特に問題なし | |||
==== (config-if)# stackwise-virtual link 1 <ref>Configuring Cisco StackWise Virtual Link<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_wly_zyx_31b | |||
Step 4 | |||
Device(config-if)#stackwise-virtual link 1 | |||
'''Step 7''' | |||
Device#reload</ref> ==== | |||
* VSS とは異なり、SWV では SVL の増速に reload が必要になりました | |||
==== (config-if)# stackwise-virtual dual-active-detection <ref>Configuring StackWise Virtual Fast Hello Dual-Active-Detection Link<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_yqn_bzx_31b</ref>==== | |||
* VSS とは異なり、SWV では DAD の設定に reload が必要になりました | |||
==== stackwise-virtual -> dual-active detection pagp <ref>Enabling ePAgP Dual-Active-Detection<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_ump_ptf_r1b</ref>==== | |||
* dual-active detection pagp trust channel-group channel-group <id> の追加に再起動が必要無いか、要調査 | |||
==== switch stack-speed [high | low] ==== | |||
* C9300X から導入された、StackWise-1T を、C9300 の StackWise-480 に混在させるためのコマンド | |||
=== Catalyst 9400 === | |||
==== (config-if)# enable <ref>アップリンク ポート<nowiki/>https://www.cisco.com/c/ja_jp/td/docs/switches/lan/catalyst9400/software/release/17-3/configuration_guide/int_hw/b_173_int_and_hw_9400_cg/configuring_interface_characteristics.html#concept_ayd_y5q_p1b | |||
速度 10G、25G、および 40G はポートグループごとに相互に排他的です。 | |||
ポートグループでは任意の 1 つの速度をいつでも有効にできます。</ref>==== | |||
* スーパーバイザエンジンの'''再起動は必要ない'''けど、ポートグループごとに速度は 1 つに制限される模様 | |||
=== Catalyst 9500 === | |||
==== hw-module breakout module ==== | |||
* 9600 を見たあとだといかにも必要そうだが、'''この機種は reload が必要ない'''模様 | |||
=== Catalyst 9600 === | |||
==== hw-module breakout-enable <ref>Configuring a Breakout Interface<nowiki/>https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/17-2/configuration_guide/int_hw/b_172_int_and_hw_9600_cg/configuring_interface_characteristics.html#task_slc_34x_1jb | |||
Step 3 | |||
hw-module breakout-enable | |||
'''Step 5''' | |||
reload</ref> ==== | |||
* 運用に入ってから再起動が必要とわかるとめんどい | |||
* グローバル コンフィグの部分で再起動が必要に見えるため、予め入れといたほうが良さそう | |||
=== Catalyst 9400X / 9500X / 9600X === | |||
Silicon One の X 系は SWV の SVL / DAD の変更で再起動が必要なくなりました <ref>[https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-10/configuration_guide/ha/b_1710_ha_9500_cg/configuring_cisco_stackwise_virtual.html#configuring_cisco_stackwise_virtual_link Dynamic addition and removal of SVL links are supported on the C9500X-28C8D model of Cisco Catalyst 9500 Series Switches, and therefore, a reload is not required for adding or removing the SVL links when the device is already operating in SVL mode.]</ref> | |||
=== Nexus3000 <ref>[https://community.cisco.com/t5/tkb-%E3%83%87%E3%83%BC%E3%82%BF%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC-%E3%83%89%E3%82%AD%E3%83%A5%E3%83%A1%E3%83%B3%E3%83%88/nexus-%E3%82%B7%E3%83%AA%E3%83%BC%E3%82%BA-cvr-qsfp-sfp10g-%E3%81%AE%E5%88%A9%E7%94%A8%E6%96%B9%E6%B3%95%E3%81%AB%E3%81%A4%E3%81%84%E3%81%A6/ta-p/3689358#toc-hId-1189404436 Nexus 3000 シリーズ] | |||
switch(config)# hardware profile portmode ? | |||
48x10g+4x40g 48x10G+4x40G port mode | |||
52x10g+3x40g 52x10G+3x40G port mode | |||
56x10g+2x40g 56x10G+2x40G port mode | |||
60x10g+1x40g 60x10G+1x40G port mode | |||
64x10g 64x10G port mode</ref> === | |||
==== hardware profile portmode <port_mode> ==== | |||
=== Nexus 3100 <ref>[https://community.cisco.com/t5/tkb-%E3%83%87%E3%83%BC%E3%82%BF%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC-%E3%83%89%E3%82%AD%E3%83%A5%E3%83%A1%E3%83%B3%E3%83%88/nexus-%E3%82%B7%E3%83%AA%E3%83%BC%E3%82%BA-cvr-qsfp-sfp10g-%E3%81%AE%E5%88%A9%E7%94%A8%E6%96%B9%E6%B3%95%E3%81%AB%E3%81%A4%E3%81%84%E3%81%A6/ta-p/3689358#toc-hId--618050027 Nexus 3100/3200 シリーズ] | |||
switch(config)# interface breakout module 1 port 49 map 10g-4x | |||
Interface breakout configured. Please poweroff and no poweroff the module</ref> === | |||
==== 例) interface breakout module 1 port 49 map 10g-4x ==== | |||
=== Nexus 5600/6000 <ref>[https://community.cisco.com/t5/tkb-%E3%83%87%E3%83%BC%E3%82%BF%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC-%E3%83%89%E3%82%AD%E3%83%A5%E3%83%A1%E3%83%B3%E3%83%88/nexus-%E3%82%B7%E3%83%AA%E3%83%BC%E3%82%BA-cvr-qsfp-sfp10g-%E3%81%AE%E5%88%A9%E7%94%A8%E6%96%B9%E6%B3%95%E3%81%AB%E3%81%A4%E3%81%84%E3%81%A6/ta-p/3689358#toc-hId-1869462806 Nexus 5600/6000 シリーズ] | |||
switch(config)# interface breakout slot 2 port 1-4 map 10g-4x | |||
Interface breakout configured. Please poweroff and no poweroff the module | |||
</ref> === | |||
==== 例) interface breakout slot 2 port 1-4 map 10g-4x ==== | |||
=== Nexus 7000 / 7700 <ref>[https://community.cisco.com/t5/tkb-%E3%83%87%E3%83%BC%E3%82%BF%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC-%E3%83%89%E3%82%AD%E3%83%A5%E3%83%A1%E3%83%B3%E3%83%88/nexus-%E3%82%B7%E3%83%AA%E3%83%BC%E3%82%BA-cvr-qsfp-sfp10g-%E3%81%AE%E5%88%A9%E7%94%A8%E6%96%B9%E6%B3%95%E3%81%AB%E3%81%A4%E3%81%84%E3%81%A6/ta-p/3689358#toc-hId-62008343 Nexus 7000/7700 シリーズ]</ref> === | |||
==== 例) interface breakout slot 2 port 1-4 map 10g-4x ==== | |||
=== Nexus9000 共通 === | |||
==== fips mode enable <ref>[https://www.cisco.com/c/en/us/td/docs/dcn/nx-os/nexus9000/105x/configuration/security/cisco-nexus-9000-series-nx-os-security-configuration-guide-release-105x/m-configuring-fips.html Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 10.5(x)]</ref> ==== | |||
'''hardware access-list tcam label''' <ref>[https://www.cisco.com/c/en/us/td/docs/dcn/nx-os/nexus9000/105x/configuration/security/cisco-nexus-9000-series-nx-os-security-configuration-guide-release-105x/m-configuring-ip-acls.html Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 10.5(x)] | |||
Chapter: Configuring IP ACLs | |||
The label size can be increased to 62 when you enter the '''hardware access-list tcam label ing-ifacl 6''' command and reload the switch.</ref> | |||
==== hardware access-list tcam region <feature_name> <feature_size> <ref>Understand how to Carve TCAM Space - Nexus 9000<nowiki/>https://www.cisco.com/c/en/us/support/docs/switches/nexus-9000-series-switches/119032-nexus9k-tcam-00.html#anc7 | |||
Configuration | |||
In order to reconfigure a TCAM region, use the | |||
hardware access-list tcam region <feature_name> | |||
<feature_size> command in the configuration terminal. | |||
Once you have changed the regions to be the intended sizes, | |||
'''you must reload the device.''' </ref> ==== | |||
* TCAM の領域を変更するコマンド 要再起動 | |||
* [https://community.cisco.com/t5/%E3%83%87%E3%83%BC%E3%82%BF%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC-%E3%83%89%E3%82%AD%E3%83%A5%E3%83%A1%E3%83%B3%E3%83%88/nexus-9000%E3%82%B7%E3%83%AA%E3%83%BC%E3%82%BA-tcam-region-%E3%81%AE%E8%A8%AD%E5%AE%9A-tcam-resource-%E3%81%AE%E7%A2%BA%E8%AA%8D%E6%96%B9%E6%B3%95%E3%81%AB%E3%81%A4%E3%81%84%E3%81%A6/ta-p/3163235 IPv6 ACL を設定するときは、デフォルトが 0 のケース]があり、領域を割り当てる必要があります | |||
==== max-metric router-lsa external-lsa include-stub on-startup summary-lsa ==== | |||
* コマンド投入後、次回の再起動時に有効になる旨のメッセージが表示されます | |||
* ただ、これは起動時に発動するコマンドのため、reload が必要とは違う気がします | * ただ、これは起動時に発動するコマンドのため、reload が必要とは違う気がします | ||
==== system vlan <vlan-id> reserve <ref>[https://www.cisco.com/c/en/us/td/docs/dcn/nx-os/nexus9000/105x/configuration/layer-2-switching/cisco-nexus-9000-series-nx-os-layer-2-switching-configuration-guide-105x/m-configuring-vlans.html Cisco Nexus 9000 Series NX-OS Layer 2 Switching Configuration Guide, Release 10.5(x)] | |||
Chapter: Configuring VLANs | |||
About Reserved VLANs | |||
The new reserved range takes effect after the running configuration is saved and the device is reloaded.</ref> ==== | |||
* Nexus がデフォルトで使用できない Vlan-ID の 3968 ~ 4095 を、別の Vlan-ID に変更するコマンド | |||
* 1 個指定すると、続けて 127 個、合計 128 個の Vlan-ID が使用できなくなる | |||
* Nexus 3000 , 5000 , 7000 でも使用可能 | |||
[https://www.cisco.com/c/ja_jp/td/docs/dcn/nx-os/nexus9000/102x/configuration/layer-2-switching/cisco-nexus-9000-nx-os-layer-2-switching-configuration-guide-102x/m-configuring-vlans.html#concept_D5ED0AAC38C94ED2B8DFFE88B4951EF2 VLAN 予約の例] | |||
************************************************** | |||
CONFIGURE NON-DEFAULT RANGE, "COPY R S" AND RELOAD | |||
************************************************** | |||
switch(config)# system vlan 400 reserve | |||
"vlan configuration 400-527" will be deleted automatically. | |||
Vlans, SVIs and sub-interface encaps for vlans 400-527 need to be removed by the user. | |||
Continue anyway? (y/n) [no] y | |||
Note: After switch reload, VLANs 400-527 will be reserved for internal use. | |||
This requires copy running-config to startup-config before | |||
switch reload. Creating VLANs within this range is not allowed. | |||
switch(config)# show system vlan reserved | |||
system current running vlan reservation: 3968-4095 | |||
system future running vlan reservation: 400-527 | |||
switch(config)# copy running-config startup-config | |||
[########################################] 100% | |||
switch(config)# reload | |||
This command will reboot the system. (y/n)? [n] y | |||
************ | |||
AFTER RELOAD | |||
************ | |||
switch# show system vlan reserved | |||
system current running vlan reservation: 400-527 | |||
=== Nexus9200 <ref name=":2">[https://www.cisco.com/c/ja_jp/td/docs/switches/datacenter/nexus9000/sw/93x/scalability/guide-935/cisco-nexus-9000-series-nx-os-verified-scalability-guide-935.html Cisco Nexus 9000 シリーズ NX-OS 検証済みスケーラビリティ ガイド リリース 9.3(5)]</ref> <ref name=":3">[https://www.cisco.com/c/ja_jp/td/docs/switches/datacenter/nexus9000/sw/93x/unicast/configuration/guide/b-cisco-nexus-9000-series-nx-os-unicast-routing-configuration-guide-93x/b-cisco-nexus-9000-series-nx-os-unicast-routing-configuration-guide-93x_chapter_011001.html Cisco Nexus 9000 シリーズ NX-OS ユニキャスト ルーティング設定ガイド]</ref> === | |||
==== system routing template-dual-stack-host-scale ==== | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-l2-heavy ==== | |||
=== Nexus 9300 <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-l2-heavy ==== | |||
==== system routing max-mode l3 ==== | |||
=== Nexus9300-EX <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-dual-stack-host-scale ==== | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-internet-peering ==== | |||
==== system routing template-l2-heavy ==== | |||
=== Nexus9300-FX <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-internet-peering ==== | |||
==== system routing template-dual-stack-host-scale ==== | |||
=== Nexus9300-FX2 <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-internet-peering ==== | |||
==== system routing template-dual-stack-host-scale ==== | |||
=== Nexus9300-GX <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-internet-peering ==== | |||
==== system routing template-dual-stack-host-scale ==== | |||
=== Nexus-9500 用 9700-EX or 9700-FX ラインカード <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing max-mode host ==== | |||
==== system routing non-hierarchical-routing [max-l3-mode] ==== | |||
==== system routing mode hierarchical 64b-alpm ==== | |||
==== system routing template-lpm-heavy ==== | |||
==== system routing template-internet-peering ==== | |||
=== Nexus-9500-R 用 9600-R ラインカード <ref name=":2" /> <ref name=":3" /> === | |||
==== system routing template-internet-peering ==== | |||
== Juniper == | |||
=== MX204 === | |||
ポートの割当を変更したい場合は、以下を参照。変更後は PIC のリセットが必要。 | |||
==== set chassis fpc <fpc_num> pic <pic_num> port <port_num> speed <speed> <ref>Port Speed on MX204 Overview<nowiki/>https://www.juniper.net/documentation/us/en/software/junos/interfaces-ethernet/topics/topic-map/port-speed-configuration.html#concept-mx204 | |||
To change the default speed, you must select a port | |||
and configure a different port speed on it | |||
and '''reset both the PICs for the configuration to take effect.''' | |||
For example, select 40GE or 100GE on PIC0 and 10GE on PIC1. | |||
For this configuration to take effect, you must reset both PICs.</ref> ==== | |||
* シャーシ全体の再起動 + Junos 起動は必要無いけど、両方の PIC = 全ポートを Offline + Online で reset する必要あり | |||
* [https://www.juniper.net/documentation/us/en/software/junos/cli-reference/topics/ref/command/request-chassis-pic.html request chassis pic] | |||
==== [https://www.juniper.net/documentation/us/en/software/junos/interfaces-ethernet/topics/topic-map/port-speed-mx-routers.html Port Speed on MX Routers] ==== | |||
<syntaxhighlight lang="diff"> | |||
Table 1: Port Speed for MX204 | |||
PIC Port Port Speed Supported | |||
PIC 0 0-3 4x10-Gigabit Ethernet | |||
40-Gigabit Ethernet | |||
100-Gigabit Ethernet | |||
Default: 4x10-Gigabit Ethernet | |||
Supports 1-Gbps speed on 10 Gigabit Ethernet ports (Junos OS Release 18.1 onwards) | |||
PIC 1 0-7 10-Gigabit Etherner | |||
Supports 1-Gbps speed on 10 Gigabit Ethernet ports (Junos OS Release 18.1 onwards) | |||
</syntaxhighlight>[https://www.juniper.net/documentation/en_US/day-one-books/DO_MX5G.pdf Figure 1.3 MX204 Packet Forwarding Engine] | |||
[[ファイル:MX204_PFE.png|代替文=MX204 PFE|なし|フレーム|MX204 PFE]] | |||
==== [https://www.juniper.net/documentation/us/en/software/junos/interfaces-ethernet/topics/topic-map/configure-port.html#xd_44b04e84b48f8267--22641f22-18c8148309f--7fb1__section_d2k_thb_dzb Configure Port Speed - PIC Level] ==== | |||
==== [https://apps.juniper.net/port-checker/mx204/ MX204 Port Checker] ==== | |||
=== MX304 === | |||
ポートの割当を変更したい場合は、以下を参照。変更後は PIC のリセットが必要。 | |||
==== [https://community.juniper.net/blogs/reema-ray/2023/03/28/mx304-deepdive MX304 Deepdive] ==== | |||
<syntaxhighlight lang="diff"> | |||
PIC Mode / Port Mode | |||
Examples (X varies from 1 to 16 depending on the port speed): | |||
set chassis fpc 0 pic0 pic-mode 100g number-of-ports X | |||
set chassis fpc 0 pic0 pic-mode 400g number-of-ports X | |||
set chassis fpc 0 pic0 pic-mode 10g number-of-ports X | |||
set chassis fpc 0 pic0 pic-mode 25g number-of-ports X | |||
set chassis fpc 0 pic0 pic-mode 50g number-of-ports X | |||
</syntaxhighlight> | |||
==== [https://apps.juniper.net/port-checker/mx304/ MX304 Port Checker] ==== | |||
=== PIC リセット コマンド例 === | |||
<syntaxhighlight lang="diff"> | |||
request chassis pic pic-slot 0 fpc-slot 0 offline | |||
request chassis pic pic-slot 0 fpc-slot 0 online | |||
</syntaxhighlight> | |||
== Arista == | == Arista == | ||
=== | ==== zerotouch cancel <ref>Canceling Zero Touch Provisioning | ||
https://www.arista.com/en/um-eos/eos-initial-switch-access#xx1131266 | |||
To avoid entering ZTP mode on subsequent reboots, create a startup-config file as described in Step 8 of Ethernet Management Port.</ref> ==== | |||
* 最初は startup-config が存在しないため、ZTP モードで起動する | |||
* cancel すると自動で再起動がかかる | |||
==== service routing protocols model { ribd | multi-agent } <ref><syntaxhighlight lang="diff"> | |||
localhost(config)#service routing protocols model multi-agent | |||
! Change will take effect only after switch reboot | |||
localhost(config)# | |||
</syntaxhighlight></ref>==== | |||
* 2022/09 現在は ribd がデフォルト | |||
* 最近は multi-agent を使うのが主流 | |||
* EVPN などでは multi-agent を使用する必要がある | |||
=== DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R === | === DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R === | ||
< | ==== hardware access-list mechanism tcam <ref>Support for Private VLAN | ||
https://www.arista.com/en/um-eos/eos-virtual-lans-vlans?searchword=reload | |||
On DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R | On DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R | ||
Private VLAN and Algomatch features are mutually exclusive. Disable algomatch with the hardware access-list mechanism tcam command . Note that this requires a reload of the system to take effect.</ref> | Private VLAN and Algomatch features are mutually exclusive. Disable algomatch with the hardware access-list mechanism tcam command . Note that '''this requires a reload''' of the system to take effect.</ref> ==== | ||
=== 7050X3 === | |||
[https://arista.my.site.com/AristaCommunity/s/article/7050X3-Logical-Port 7050X3でのLogical Portの管理]<syntaxhighlight lang="diff"> | |||
7050SX3-48YC8, 7050SX3-48C8, 7050TX3-48C8ではスイッチのLogical Portの数が64でインタフェースの総数より少なくなっています。 | |||
</syntaxhighlight> | |||
* 25G x 48 + ブレークアウト 25G x 4 波長 x 8 ポート = 80 ポートが最大だが、そのうち 64 ポートしか使えないことを意味する | |||
* platform trident reset でトラフィック中断の発生するリセットが必要な場合がある<br /> | |||
== A10 == | == A10 == | ||
Thunder 3030S CGN / 3040S CFW | A10 のマニュアルはインターネット上に公開されておらず、アカウント作成とログインが必要。 | ||
=== Thunder 3030S CGN === | |||
==== system resource-usage nat-pool-addr-count <ref>system resource-usage | |||
https://documentation.a10networks.com/ACOS/271x/271-P6/ACOS_2_7_1-P6/html/ax-cli-reference-Responsive%20HTML5/ax-cli-reference/ax-cli-globalcfg-cmds/system_resource-usage.htm?rhsearch=system%20resource-usage%20nat-pool-addr-count&rhsyns=%20 | |||
nat-pool-addr-count --- Total IP source NAT pools | |||
Reload or Reboot Required | |||
To place a change to l4-session-count into effect, a reboot is required. A reload will not place this change into effect. For changes to any of the other system resources, a reload is required but a reboot is not required.</ref> ==== | |||
* CGN 用 NAT プールアドレス | |||
=== Thunder 3040S CFW === | |||
==== system resource-usage nat-pool-addr-count <ref>system resource-usage | |||
https://documentation.a10networks.com/ACOS/414x/ACOS_4_1_4-GR1-P1/html/cli-reference-Responsive%20HTML5/cli-reference/cli-globalcfg-cmds/system_resource-usage.htm?rhsearch=system%20resource-usage&rhsyns=%20 | |||
nat-pool-addr-count num --- Total number of NAT pool addresses available for configuration in the system. The range is platform specific. | |||
Usage | |||
To place a change to l4-session-count into effect, | |||
a reboot is required. | |||
A reload will not place this change into effect. | |||
For changes to any of the other system resources, | |||
a reload is required but a reboot is not required.</ref> ==== | |||
==== system resource-usage l4-session-count <ref>ACOS 5.2.1-P8 Command Line Interface Reference Guide | |||
'''Usage''' | |||
To place a change to l4-session-count into effect, a reboot is required.</ref> ==== | |||
==== cgnv6 resource-usage lsn-nat-addr-count <ref>cgnv6 resource-usage | |||
https://documentation.a10networks.com/ACOS/414x/ACOS_4_1_4-GR1-P11/html/cliv6-Responsive%20HTML5/cliv6/cliv6_cgn_aka_lsn_cmds/cgnv6_resource-usage.htm?rhsearch=cgnv6%20resource-usage%20lsn-nat-addr-count&rhsyns=%20</ref> <ref><syntaxhighlight lang="diff"> | |||
(config)#cgnv6 resource-usage lsn-nat-addr-count 2048 | |||
Changes will come into effect next time you reload the Software. | |||
</syntaxhighlight></ref> ==== | |||
* こちらはコマンドリファレンスに reload 必須との記載が無いが、コマンドを打つと reload が必要と出てくる | |||
==== system promiscuous-mode ==== | |||
==== system-jumbo-global enable-jumbo ==== | |||
* non-FTA モデルでは変更時に reboot が必要 <ref>ACOS5.2.1-P8 | |||
Command_Line_Interface_Reference.pdf | |||
NOTE: | |||
On non-FTA models, after you enable (or disable) jumbo frame support, you must save the configuration (write memory command) and reboot (reboot command) to place the change into effect.</ref> | |||
== Extreme VSP == | |||
==== boot config flags spbm-config-mode <ref>[https://documentation.extremenetworks.com/VOSS/SW/89/VOSSUserGuide/GUID-DCBDDD6D-57E4-486A-83A9-4D33886AA891.shtml#GUID-CD735C3D-7B32-466C-BB24-973CDB3B8C94 Virtual interswitch trunk (vIST)] | |||
enable | |||
configure terminal | |||
no boot config flags spbm-config-mode | |||
Save the configuration and reboot the switch.</ref> ==== | |||
==== boot config flags advanced-feature-bandwidth-reservation <ref>[https://documentation.extremenetworks.com/FABRICENGINE/SW/810/FabricEngineUserGuide/GUID-E463D2F1-8B68-4E81-8434-36C2114F13C7.shtml If you change the configuration, you must save the configuration, and then reboot the switch for the change to take effect.]</ref> ==== | |||
* 他の boot config flags コマンドも再起動が必要なものがある | |||
== リファレンス == | |||
<references /> | |||
[[カテゴリ:その他]] | |||
2024年10月9日 (水) 19:21時点における最新版
いろいろなメーカーのネットワーク機器について、再起動しないと有効にならないコンフィグを集めました。
以下のようなシチュエーションで役に立ちます。
- 作業の役務を見積もるとき、夜間作業が必要か調べたい
- 保守交換後、OS Ver と running-config で diff が無くても、動作に差分があるとき
- TCAM サイズを変更するコマンドは、ROMMON / Boot Loader の変数に書き込まれて running-config に表示されない機器があります
- 初期構築時に設定追加・変更しておくことで運用に入ってからの停止作業を回避
Cisco
ISR4000 / ASR1000
ASR1000 : license boot level { adventerprise | advipservices | ipbase } [1]
- Universal イメージの IOS / IOS-XE はコマンドでライセンス レベルを変更可能
ISR4000 : platform hardware throughput level { 2500000 | 5000000 } [2]
ISR4000 : platform hardware throughput level boost [3]
ASR1000 : platform hardware throughput level [4]
- デフォルトは双方向で合計 2.5Gbps のスループット
- 双方向で 20Gbps の最大スループットを設定可能
- 10G ポートの Rx / Tx の合計で 20Gbps を捌けるのと、同一の意味
- CSR1000V は再起動が不要と記載あり
ASR1001-HX : platform hardware crypto-throughput level { 8g | 8-16g } [5]
- こちらは再起動が必要無いように読める
ASR1002-HX : platform hardware crypto-throughput level { 8g | 8-16g | 8-25g | 16-25g } [6]
- こちらは再起動が必要無いように読める
Catalyst8200 / 8300
platform resource { service-plane-heavy | data-plane-heavy }
- Catalyst 8200 , 8300 は複数の CPU コアを、サービス プレーンとデータプレーンに振り分ける割合を変えることが可能
- 最小 8 コアを備えている
- デフォルトは service-plane-heavy
- show platform software cpu alloc コマンドで、割り当て状況を確認可能
show platform software cpu alloc
CPU alloc information:
Control plane cpu alloc: 0
Data plane cpu alloc: 1-7
Service plane cpu alloc: 0
Template used: CLI-data_plane_heavy
platform hardware throughput crypto
platform hardware throughput level MB
(EXEC) license throughput crypto auto-convert
(EXEC) license throughput level auto-convert
Cisco 8000
hw-module profile route scale lpm tcam-banks [7]
Catalyst 2960 / 3560 / 3750
3750 : sdm prefer { access | default | dual-ipv4-and-ipv6 { default | routing | vlan } | indirect-ipv4-and-ipv6-routing | routing | vlan } [8]
- PBR / IPv6 はデフォルトで TCAM が割り当てられていないため、routing / dual stack テンプレートに変更 + 再起動が必要
system mtu jumbo <1500-9000> | <1500-9198>
- show run に出てこない
- show system mtu コマンドで確認可能
- 機種により対応範囲が異なる
- 3750G : 1500-9000
- 3560CX : 1500-9198
Catalyst 4500 Sup6E
- 要再起動
- 最初に TenGig を使っていなくて、増速で TenGig にするときに要注意
hw-module module <module_num> port-group <port_num> select [ gigabitethernet | tengigabitethernet ]
- WS-X4606-10GE-E で TwinGig コンバーターを使用するときに使用
- こちらは再起動の必要無し
Catalyst 6500 Sup720 / Sup720-10G
mls cef maximum-routes [10]
Catalyst 6500 / 6800 Sup2T / Sup6T
共通 : vlan internal allocation policy { ascending | descending } [11]
共通 : platform hardware acl reserve qos-banks { 1 | 2} [12]
Sup6T : hw-module switch {switch-id} slot {sup slot no.} operation-mode port-group {Port-group no. } { TenGigabitEthernet | FortyGigabitEthernet } [13]
Sup6T : hw-module switch {switch-id} slot {sup slot no.} performance { TenGigabitEthernet | FortyGigabitEthernet } [13]
Catalyst 3850 / 3650 / 9000
license boot level <license_level> [14]
- Universal イメージの IOS / IOS-XE はコマンドでライセンス レベルを変更可能
- グローバル コンフィギュレーションで実施
9000 : license right-to-use [activate | deactivate ] [network-essentials | network-advantage ] [all | evaluation {all | slot slot-number <1-8>}] [acceptEULA] [15]
- こちらは EXEC モードで実施
- Evaluation (評価) モードで動作している場合は、ライセンスを購入して right-to-use で Permanent モードに変更します
9000 : license right-to-use [activate | deactivate ] addon [dna-essentials | dna-advantage ] [all | evaluation | subscription {all | slot slot-number <1-8>}] [ acceptEULA] [15]
- こちらは EXEC モードで実施
- Evaluation (評価) モードで動作している場合は、ライセンスを購入して right-to-use で Permanent モードに変更します
9500 : sdm prefer { core | nat | distribution | custom } [16]
- 9500H デフォルトの Core テンプレートの場合は MAC アドレステーブルや ARP が少ないため、Distribution に変更するケースがあります
Catalyst 3850XS 16.3.3- / 9400 / 9500 / 9600
stackwise-virtual -> domain <domain_id> [17]
secure-stackwise-virtual authorization-key <128-bits> [18]
- 初期設定時のみと思われるため、特に問題なし
(config-if)# stackwise-virtual link 1 [19]
- VSS とは異なり、SWV では SVL の増速に reload が必要になりました
(config-if)# stackwise-virtual dual-active-detection [20]
- VSS とは異なり、SWV では DAD の設定に reload が必要になりました
stackwise-virtual -> dual-active detection pagp [21]
- dual-active detection pagp trust channel-group channel-group <id> の追加に再起動が必要無いか、要調査
switch stack-speed [high | low]
- C9300X から導入された、StackWise-1T を、C9300 の StackWise-480 に混在させるためのコマンド
Catalyst 9400
(config-if)# enable [22]
- スーパーバイザエンジンの再起動は必要ないけど、ポートグループごとに速度は 1 つに制限される模様
Catalyst 9500
hw-module breakout module
- 9600 を見たあとだといかにも必要そうだが、この機種は reload が必要ない模様
Catalyst 9600
hw-module breakout-enable [23]
- 運用に入ってから再起動が必要とわかるとめんどい
- グローバル コンフィグの部分で再起動が必要に見えるため、予め入れといたほうが良さそう
Catalyst 9400X / 9500X / 9600X
Silicon One の X 系は SWV の SVL / DAD の変更で再起動が必要なくなりました [24]
Nexus3000 [25]
hardware profile portmode <port_mode>
Nexus 3100 [26]
例) interface breakout module 1 port 49 map 10g-4x
Nexus 5600/6000 [27]
例) interface breakout slot 2 port 1-4 map 10g-4x
Nexus 7000 / 7700 [28]
例) interface breakout slot 2 port 1-4 map 10g-4x
Nexus9000 共通
fips mode enable [29]
hardware access-list tcam label [30]
hardware access-list tcam region <feature_name> <feature_size> [31]
- TCAM の領域を変更するコマンド 要再起動
- IPv6 ACL を設定するときは、デフォルトが 0 のケースがあり、領域を割り当てる必要があります
max-metric router-lsa external-lsa include-stub on-startup summary-lsa
- コマンド投入後、次回の再起動時に有効になる旨のメッセージが表示されます
- ただ、これは起動時に発動するコマンドのため、reload が必要とは違う気がします
system vlan <vlan-id> reserve [32]
- Nexus がデフォルトで使用できない Vlan-ID の 3968 ~ 4095 を、別の Vlan-ID に変更するコマンド
- 1 個指定すると、続けて 127 個、合計 128 個の Vlan-ID が使用できなくなる
- Nexus 3000 , 5000 , 7000 でも使用可能
**************************************************
CONFIGURE NON-DEFAULT RANGE, "COPY R S" AND RELOAD
**************************************************
switch(config)# system vlan 400 reserve
"vlan configuration 400-527" will be deleted automatically.
Vlans, SVIs and sub-interface encaps for vlans 400-527 need to be removed by the user.
Continue anyway? (y/n) [no] y
Note: After switch reload, VLANs 400-527 will be reserved for internal use.
This requires copy running-config to startup-config before
switch reload. Creating VLANs within this range is not allowed.
switch(config)# show system vlan reserved
system current running vlan reservation: 3968-4095
system future running vlan reservation: 400-527
switch(config)# copy running-config startup-config
[########################################] 100%
switch(config)# reload
This command will reboot the system. (y/n)? [n] y
************
AFTER RELOAD
************
switch# show system vlan reserved
system current running vlan reservation: 400-527
Nexus9200 [33] [34]
system routing template-dual-stack-host-scale
system routing template-lpm-heavy
system routing template-l2-heavy
Nexus 9300 [33] [34]
system routing template-l2-heavy
system routing max-mode l3
Nexus9300-EX [33] [34]
system routing template-dual-stack-host-scale
system routing template-lpm-heavy
system routing template-internet-peering
system routing template-l2-heavy
Nexus9300-FX [33] [34]
system routing template-lpm-heavy
system routing template-internet-peering
system routing template-dual-stack-host-scale
Nexus9300-FX2 [33] [34]
system routing template-lpm-heavy
system routing template-internet-peering
system routing template-dual-stack-host-scale
Nexus9300-GX [33] [34]
system routing template-lpm-heavy
system routing template-internet-peering
system routing template-dual-stack-host-scale
Nexus-9500 用 9700-EX or 9700-FX ラインカード [33] [34]
system routing max-mode host
system routing non-hierarchical-routing [max-l3-mode]
system routing mode hierarchical 64b-alpm
system routing template-lpm-heavy
system routing template-internet-peering
Nexus-9500-R 用 9600-R ラインカード [33] [34]
system routing template-internet-peering
Juniper
MX204
ポートの割当を変更したい場合は、以下を参照。変更後は PIC のリセットが必要。
set chassis fpc <fpc_num> pic <pic_num> port <port_num> speed <speed> [35]
- シャーシ全体の再起動 + Junos 起動は必要無いけど、両方の PIC = 全ポートを Offline + Online で reset する必要あり
- request chassis pic
Port Speed on MX Routers
Table 1: Port Speed for MX204
PIC Port Port Speed Supported
PIC 0 0-3 4x10-Gigabit Ethernet
40-Gigabit Ethernet
100-Gigabit Ethernet
Default: 4x10-Gigabit Ethernet
Supports 1-Gbps speed on 10 Gigabit Ethernet ports (Junos OS Release 18.1 onwards)
PIC 1 0-7 10-Gigabit Etherner
Supports 1-Gbps speed on 10 Gigabit Ethernet ports (Junos OS Release 18.1 onwards)
Figure 1.3 MX204 Packet Forwarding Engine
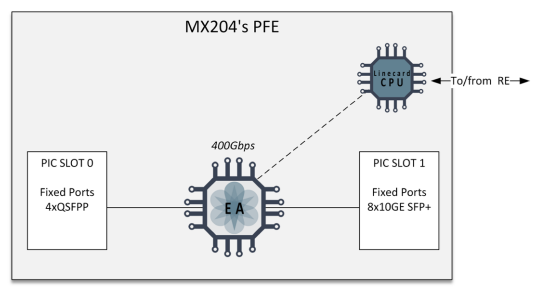
Configure Port Speed - PIC Level
MX204 Port Checker
MX304
ポートの割当を変更したい場合は、以下を参照。変更後は PIC のリセットが必要。
MX304 Deepdive
PIC Mode / Port Mode
Examples (X varies from 1 to 16 depending on the port speed):
set chassis fpc 0 pic0 pic-mode 100g number-of-ports X
set chassis fpc 0 pic0 pic-mode 400g number-of-ports X
set chassis fpc 0 pic0 pic-mode 10g number-of-ports X
set chassis fpc 0 pic0 pic-mode 25g number-of-ports X
set chassis fpc 0 pic0 pic-mode 50g number-of-ports X
MX304 Port Checker
PIC リセット コマンド例
request chassis pic pic-slot 0 fpc-slot 0 offline
request chassis pic pic-slot 0 fpc-slot 0 online
Arista
zerotouch cancel [36]
- 最初は startup-config が存在しないため、ZTP モードで起動する
- cancel すると自動で再起動がかかる
service routing protocols model { ribd | multi-agent } [37]
- 2022/09 現在は ribd がデフォルト
- 最近は multi-agent を使うのが主流
- EVPN などでは multi-agent を使用する必要がある
DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R
hardware access-list mechanism tcam [38]
7050X3
7050SX3-48YC8, 7050SX3-48C8, 7050TX3-48C8ではスイッチのLogical Portの数が64でインタフェースの総数より少なくなっています。
- 25G x 48 + ブレークアウト 25G x 4 波長 x 8 ポート = 80 ポートが最大だが、そのうち 64 ポートしか使えないことを意味する
- platform trident reset でトラフィック中断の発生するリセットが必要な場合がある
A10
A10 のマニュアルはインターネット上に公開されておらず、アカウント作成とログインが必要。
Thunder 3030S CGN
system resource-usage nat-pool-addr-count [39]
- CGN 用 NAT プールアドレス
Thunder 3040S CFW
system resource-usage nat-pool-addr-count [40]
system resource-usage l4-session-count [41]
cgnv6 resource-usage lsn-nat-addr-count [42] [43]
- こちらはコマンドリファレンスに reload 必須との記載が無いが、コマンドを打つと reload が必要と出てくる
system promiscuous-mode
system-jumbo-global enable-jumbo
- non-FTA モデルでは変更時に reboot が必要 [44]
Extreme VSP
boot config flags spbm-config-mode [45]
boot config flags advanced-feature-bandwidth-reservation [46]
- 他の boot config flags コマンドも再起動が必要なものがある
リファレンス
- ↑ Chapter: License Verification https://www.cisco.com/c/en/us/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG/b_ASR1001HX-1002HX_HIG_chapter_0110.html license boot level <License_Level>
- ↑ Performance https://www.cisco.com/c/en/us/td/docs/routers/access/4400/software/configuration/guide/isr4400swcfg/bm_isr_4400_sw_config_guide_chapter_0101.html#concept_3F15D3B0CBA64CA9BADC3C84FE0C63FB To configure the throughput level, perform the following steps and to upgrade the throughput level use the platform hardware throughput level { 2500000 | 5000000} command. In the user EXEC configuration mode, enter the enable command. Enter configure terminal command to enter the global configuration mode. To upgrade the throughput level, enter the platform hardware throughput level{2500000|5000000} command. To exit global configuration mode, enter exit. To save the configuration, enter the copy running-config startup-config command. To reload the router enter reload. A reload is required to activate the throughput level.
- ↑ platform hardware throughput level boost https://www.cisco.com/c/en/us/td/docs/routers/access/4400/software/configuration/guide/isr4400swcfg/bm_isr_4400_sw_config_guide_chapter_0101.html#concept_x2p_pkj_ndb Save the configuration and reload the device to enable Boost performance license. After the reload, the Boost Performance is activated as shown in this example.
- ↑ スループット レベルの設定 https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001-x/asr1hig-book/asr1hig-book_chapter_0101.html#con_1060881 Cisco ASR 1001-X ルータの組み込みエンベデッド サービス プロセッサは、ソフトウェア ライセンスに応じて、2.5 Gbps(デフォルト)、5 Gbps、10 Gbps、および 20 Gbps のスループットをサポートします。 ソフトウェア アクティベーションによるパフォーマンス アップグレード ライセンスを適用してから、ルータをリロードすることによって、ESP のスループットを 2.5 Gbps(デフォルト)から 5 Gbps にアップグレードできます。ESP のスループットは、任意のライセンス レベルから別のライセンス レベルにアップグレードできます。 ESP の現在のスループットレベルを決定するには、show platform hardware throughput level コマンドを実行します。 次に、20 Gbps パフォーマンス アップグレード ライセンスの適用とルータのリロード後の このコマンドの出力例を示します。
- ↑ 暗号化スループット レベルの設定https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG.pdf
Cisco ASR 1001-HX ルータの暗号化スループット レベルを設定するには、次のコマンドを入力します。
Router(config)# platform hardware crypto-throughput level ? 8-16g crypto throughput upgrade, bits per second 8g crypto throughput level, bits per second Router(config)# platform hardware crypto-throughput level 8g % Crypto Bandwidth set to 8G bps. Router(config)# platform hardware crypto-throughput level 8-16g % Crypto Bandwidth set to 16G bps.
- ↑ 暗号化スループット レベルの設定https://www.cisco.com/c/ja_jp/td/docs/routers/asr1000/install/guide/1001HX_1002HX/b_ASR1001HX-1002HX_HIG.pdf
Cisco ASR 1002-HX ルータの暗号化スループット レベルを設定するには、次のコマンドを入力します。
Router(config)# platform hardware crypto-throughput level ? 16-25g crypto throughput upgrade, bits per second 8-16g crypto throughput upgrade, bits per second 8-25g crypto throughput upgrade, bits per second 8g crypto throughput level, bits per second
- ↑ hw-module profile route scale
- ↑ Chapter: Configuring SDM Templates https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/15-0_2_se/configuration/guide/3750x_cg/swsdm.html
- ↑ Supervisor Engine 6-E でのアップリンク モードの選択 https://www.cisco.com/c/ja_jp/td/docs/sw/lanswt-access/cat4500swt/cg/009/confg-gd/sw-int.html#18105 (注) hw-module uplink mode shared-backplane コマンドを使用して アップリンク モードを変更する場合は、システムをリロードする必要が あります。コンソールには、リロードを示すメッセージが表示されます。
- ↑ CAT 6500 and 7600 Series Routers and Switches TCAM Allocation Adjustment Procedures https://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/117712-problemsolution-cat6500-00.html#anc3 You can enter the mls cef maximum-routes ip <number in thousands> command in order to adjust the number of routing entries that are allocated to the IPv4. This does not increase the overall size of the FIB TCAM, but it reduces the number of routing entries that are allocated to the IPv6 in order to increase the amount of TCAM space for the IPv4.
- ↑ Configuring the Internal VLAN Allocation Policyhttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf Note The internal VLAN allocation policy is applied only following a reload.
- ↑ Chapter 23 Restrictions for PFC QoShttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf Changes to the supported number of QoS TCAM entries take effect after a reload. Enter the show platform hardware acl global-config command to display the QoS TCAM entry configuration:
- ↑ 13.0 13.1 Chapter 4 Virtual Switching Systemshttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/15-5SY/config_guide/sup6T/15_5_sy_swcg_6T.pdf Note - The entire systems reloads after any mode conversion.
- ↑ Configuring Base and Add-On Licenses https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/17-6/configuration_guide/sys_mgmt/b_176_sys_mgmt_9300_cg/licenses.html#Cisco_Task.dita_f126c327-a647-4235-b1a2-930771e49f9d license boot level <license_level>
- ↑ 15.0 15.1 Activating a License
- ↑ Chapter: Configuring SDM Templates https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-6/configuration_guide/sys_mgmt/b_176_sys_mgmt_9500_cg/configuring_sdm_templates.html
- ↑ Configuring Cisco StackWise Virtual Settings https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_lbj_yyx_31b Step 5 Device(config)#stackwise-virtual Step 6 Device(config-stackwise-virtual)#domain 2 Step 10 reload
- ↑ Configuring Secure StackWise Virtual
Step 3
secure-stackwise-virtual authorization-key <128-bits>
Example:
Device(config)#secure-stackwise-virtual authorization-key <128-bits>Step 4 reload Example:Device#reload - ↑ Configuring Cisco StackWise Virtual Linkhttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_wly_zyx_31b Step 4 Device(config-if)#stackwise-virtual link 1 Step 7 Device#reload
- ↑ Configuring StackWise Virtual Fast Hello Dual-Active-Detection Linkhttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_yqn_bzx_31b
- ↑ Enabling ePAgP Dual-Active-Detectionhttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9500/software/release/17-3/configuration_guide/ha/b_173_ha_9500_cg/configuring_cisco_stackwise_virtual.html#task_ump_ptf_r1b
- ↑ アップリンク ポートhttps://www.cisco.com/c/ja_jp/td/docs/switches/lan/catalyst9400/software/release/17-3/configuration_guide/int_hw/b_173_int_and_hw_9400_cg/configuring_interface_characteristics.html#concept_ayd_y5q_p1b 速度 10G、25G、および 40G はポートグループごとに相互に排他的です。 ポートグループでは任意の 1 つの速度をいつでも有効にできます。
- ↑ Configuring a Breakout Interfacehttps://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/17-2/configuration_guide/int_hw/b_172_int_and_hw_9600_cg/configuring_interface_characteristics.html#task_slc_34x_1jb Step 3 hw-module breakout-enable Step 5 reload
- ↑ Dynamic addition and removal of SVL links are supported on the C9500X-28C8D model of Cisco Catalyst 9500 Series Switches, and therefore, a reload is not required for adding or removing the SVL links when the device is already operating in SVL mode.
- ↑ Nexus 3000 シリーズ switch(config)# hardware profile portmode ? 48x10g+4x40g 48x10G+4x40G port mode 52x10g+3x40g 52x10G+3x40G port mode 56x10g+2x40g 56x10G+2x40G port mode 60x10g+1x40g 60x10G+1x40G port mode 64x10g 64x10G port mode
- ↑ Nexus 3100/3200 シリーズ switch(config)# interface breakout module 1 port 49 map 10g-4x Interface breakout configured. Please poweroff and no poweroff the module
- ↑ Nexus 5600/6000 シリーズ switch(config)# interface breakout slot 2 port 1-4 map 10g-4x Interface breakout configured. Please poweroff and no poweroff the module
- ↑ Nexus 7000/7700 シリーズ
- ↑ Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 10.5(x)
- ↑ Cisco Nexus 9000 Series NX-OS Security Configuration Guide, Release 10.5(x) Chapter: Configuring IP ACLs The label size can be increased to 62 when you enter the hardware access-list tcam label ing-ifacl 6 command and reload the switch.
- ↑ Understand how to Carve TCAM Space - Nexus 9000https://www.cisco.com/c/en/us/support/docs/switches/nexus-9000-series-switches/119032-nexus9k-tcam-00.html#anc7 Configuration In order to reconfigure a TCAM region, use the hardware access-list tcam region <feature_name> <feature_size> command in the configuration terminal. Once you have changed the regions to be the intended sizes, you must reload the device.
- ↑ Cisco Nexus 9000 Series NX-OS Layer 2 Switching Configuration Guide, Release 10.5(x) Chapter: Configuring VLANs About Reserved VLANs The new reserved range takes effect after the running configuration is saved and the device is reloaded.
- ↑ 33.0 33.1 33.2 33.3 33.4 33.5 33.6 33.7 Cisco Nexus 9000 シリーズ NX-OS 検証済みスケーラビリティ ガイド リリース 9.3(5)
- ↑ 34.0 34.1 34.2 34.3 34.4 34.5 34.6 34.7 Cisco Nexus 9000 シリーズ NX-OS ユニキャスト ルーティング設定ガイド
- ↑ Port Speed on MX204 Overviewhttps://www.juniper.net/documentation/us/en/software/junos/interfaces-ethernet/topics/topic-map/port-speed-configuration.html#concept-mx204 To change the default speed, you must select a port and configure a different port speed on it and reset both the PICs for the configuration to take effect. For example, select 40GE or 100GE on PIC0 and 10GE on PIC1. For this configuration to take effect, you must reset both PICs.
- ↑ Canceling Zero Touch Provisioning https://www.arista.com/en/um-eos/eos-initial-switch-access#xx1131266 To avoid entering ZTP mode on subsequent reboots, create a startup-config file as described in Step 8 of Ethernet Management Port.
- ↑
localhost(config)#service routing protocols model multi-agent ! Change will take effect only after switch reboot localhost(config)# - ↑ Support for Private VLAN https://www.arista.com/en/um-eos/eos-virtual-lans-vlans?searchword=reload On DCS-7280R, DCS-7280R2, DCS-7500R, DCS-7500R2, DCS-7020R Private VLAN and Algomatch features are mutually exclusive. Disable algomatch with the hardware access-list mechanism tcam command . Note that this requires a reload of the system to take effect.
- ↑ system resource-usage https://documentation.a10networks.com/ACOS/271x/271-P6/ACOS_2_7_1-P6/html/ax-cli-reference-Responsive%20HTML5/ax-cli-reference/ax-cli-globalcfg-cmds/system_resource-usage.htm?rhsearch=system%20resource-usage%20nat-pool-addr-count&rhsyns=%20 nat-pool-addr-count --- Total IP source NAT pools Reload or Reboot Required To place a change to l4-session-count into effect, a reboot is required. A reload will not place this change into effect. For changes to any of the other system resources, a reload is required but a reboot is not required.
- ↑ system resource-usage https://documentation.a10networks.com/ACOS/414x/ACOS_4_1_4-GR1-P1/html/cli-reference-Responsive%20HTML5/cli-reference/cli-globalcfg-cmds/system_resource-usage.htm?rhsearch=system%20resource-usage&rhsyns=%20 nat-pool-addr-count num --- Total number of NAT pool addresses available for configuration in the system. The range is platform specific. Usage To place a change to l4-session-count into effect, a reboot is required. A reload will not place this change into effect. For changes to any of the other system resources, a reload is required but a reboot is not required.
- ↑ ACOS 5.2.1-P8 Command Line Interface Reference Guide Usage To place a change to l4-session-count into effect, a reboot is required.
- ↑ cgnv6 resource-usage https://documentation.a10networks.com/ACOS/414x/ACOS_4_1_4-GR1-P11/html/cliv6-Responsive%20HTML5/cliv6/cliv6_cgn_aka_lsn_cmds/cgnv6_resource-usage.htm?rhsearch=cgnv6%20resource-usage%20lsn-nat-addr-count&rhsyns=%20
- ↑
(config)#cgnv6 resource-usage lsn-nat-addr-count 2048 Changes will come into effect next time you reload the Software.
- ↑ ACOS5.2.1-P8 Command_Line_Interface_Reference.pdf NOTE: On non-FTA models, after you enable (or disable) jumbo frame support, you must save the configuration (write memory command) and reboot (reboot command) to place the change into effect.
- ↑ Virtual interswitch trunk (vIST) enable configure terminal no boot config flags spbm-config-mode Save the configuration and reboot the switch.
- ↑ If you change the configuration, you must save the configuration, and then reboot the switch for the change to take effect.