2024-09-25 Cat3850 PBR 機能検証
想定外の動作をしたりデバッグ手法の少ない PBR について、機能検証を実施しました。
このページにラボシナリオとして、コンフィグや確認コマンド、疎通確認のポイントなどをまとめています。
実機として Catalyst 3850 を使用していますが、同一系統の ASIC を持つ、Catalyst 9000 シリーズでも同様の動作をします。
目的
PBR の想定外動作について理解を深められること。
IP アドレッシングを意識した PBR 用 ACL を設計できるようになること。
通信要件
LAN グローバル アドレスが送信元のトラフィック
- WAN 宛も LAN 宛も NAT されないこと
LAN プライベート アドレスが送信元のトラフィック
- LAN グローバル / プライベート アドレス宛のトラフィックは NAT されず疎通できること
- WAN グローバル アドレス宛てのトラフィックが NAT され疎通できること
- LAN / WAN のすべての IP に対し、疎通確認と経路確認ができること
LAN プライベートアドレスが宛先のトラフィック
- WAN グローバル アドレスから、LAN プライベート アドレスに疎通できないこと
PBR 冗長
- PBR の next-hop がリンク障害時に次の next-hop へ切り替わること
検証環境
Cisco Catalyst 3850-24T : IOS-XE 16.12.12 x3
VyOS ベアメタル : 1.4-rolling-202203110317
構成図
- Catalyst 3850 : PE-RT01 , CE-RT01 , L3SW01
- VyOS : NAT-RT01
PE-RT01 を WAN の機器、CE-RT01 , NAT-RT01 , L3SW01 を LAN の機器とする。
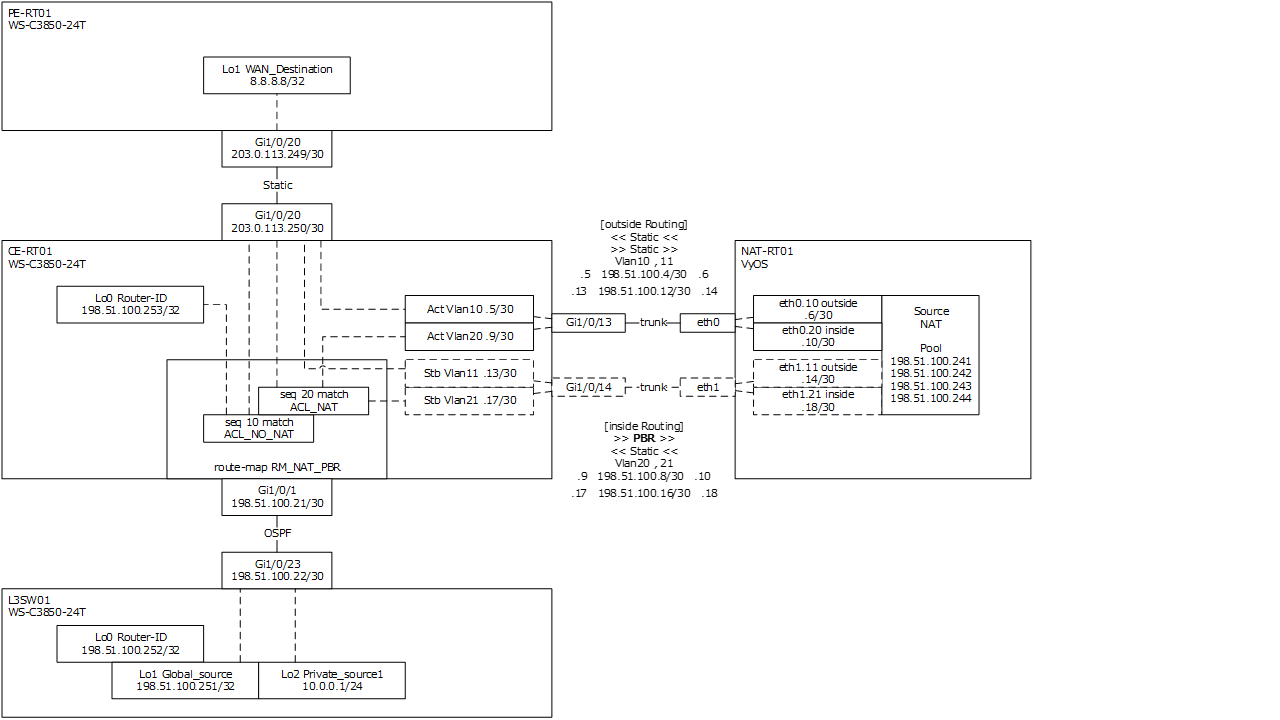
IP アドレッシング
| 文書用例示アドレス (8.8.8.8 を除く) | ||||||
|---|---|---|---|---|---|---|
| 大種別 | 小種別 | ネットワーク アドレス | ホスト | インターフェース | ホスト アドレス | 備考 |
| グローバルアドレス | WAN グローバルアドレス | 8.8.8.8/32 | PE-RT01 | Lo1 | 8.8.8.8/32 | 主な ping の宛先 |
| 203.0.113.248/30 | PE-RT01 | Gi1/0/20 | 203.0.113.249/30 | スタティック ルーティングを設定
CE ルータ宛には
| ||
| CE-RT01 | Gi1/0/20 | 203.0.113.250/30 | PE ルータ宛にデフォルト ルートを設定する | |||
| LAN グローバル アドレス | 198.51.100.0/24 | CE-RT01 | Vlan10 | 198.51.100.5/30 | NAT outside Active | |
| NAT-RT01 | eth0.10 | 198.51.100.6/30 | ||||
| CE-RT01 | Vlan20 | 198.51.100.9/30 | NAT inside Active | |||
| NAT-RT01 | eth0.20 | 198.51.100.10/30 | ||||
| CE-RT01 | Vlan11 | 198.51.100.13/30 | NAT outside Standby | |||
| NAT-RT01 | eth1.11 | 198.51.100.14/30 | ||||
| CE-RT01 | Vlan21 | 198.51.100.17/30 | NAT inside Standby | |||
| NAT-RT01 | eth1.21 | 198.51.100.18/30 | ||||
| CE-RT01 | Gi1/0/1 | 198.51.100.21/30 | OSPF で L3SW のネットワーク アドレスを受信する
デフォルトルートを配布 | |||
| L3SW01 | Gi1/0/23 | 198.51.100.22/30 | OSPF で L3SW のネットワークアドレスを配布する
デフォルトルートを受信 | |||
| L3SW01 | Lo1 | 198.51.100.251/32 | グローバル アドレスの疎通確認用 送信元 IP アドレス | |||
| プライベートアドレス | LAN プライベート アドレス | 10.0.0.0/24 | L3SW01 | Lo2 | 10.0.0.1/24 | プライベート アドレスの疎通確認用 送信元 IP アドレス |
コンフィギュレーション
ここではプロトコル・ホスト別にコンフィギュレーションを簡単に解説します。
自分でコンフィグを組んでみたい人向けに、デフォルトでは表示しません。
PE-RT01
| プロトコル | PE-RT01 コンフィグ | 解説 | |
|---|---|---|---|
| IPv4 |
interface Loopback1 description WAN_Destination ip address 8.8.8.8 255.255.255.255 interface GigabitEthernet1/0/20 description CE-RT01_Gi1/0/20 no switchport ip address 203.0.113.249 255.255.255.252 ip route 198.51.100.0 255.255.255.0 GigabitEthernet1/0/20 203.0.113.250 name CE-LAN-Loopback_P2P ip route 203.0.113.0 255.255.255.0 GigabitEthernet1/0/20 203.0.113.250 name CE-LAN-Global |
CE-RT01
| プロトコル | CE-RT01 コンフィグ | 解説 |
|---|---|---|
| インターフェース |
CE-RT01#show run | s ip route [0-9]|Loopback|1/0/20|1/0/1$|router ospf|ACL|RM|ip routing interface Loopback0 description Router-ID ip address 198.51.100.253 255.255.255.255 interface GigabitEthernet1/0/1 description L3SW01_Gi1/0/23 no switchport ip address 198.51.100.21 255.255.255.252 ip ospf network point-to-point ip policy route-map RM_NAT_PBR interface GigabitEthernet1/0/20 description RT01_Gi1/0/1 no switchport ip address 203.0.113.250 255.255.255.252 |
Loopback アドレスを LAN の ping 宛先として、プライベート IP からは NAT せずに到達できるようにする
Gi1/0/1 は下位 L3SW01 と接続し、OSPF でルート受信・配布、ip policy で PBR を動作させる Gi1/020 は上位 PE-RT01 と接続させ、スタティック ルーティングを行う |
| ルーティング |
ip routing router ospf 1 router-id 198.51.100.253 passive-interface default no passive-interface GigabitEthernet1/0/1 network 198.51.100.0 0.0.0.3 area 0.0.0.0 network 198.51.100.4 0.0.0.3 area 0.0.0.0 network 198.51.100.8 0.0.0.3 area 0.0.0.0 network 198.51.100.12 0.0.0.3 area 0.0.0.0 network 198.51.100.16 0.0.0.3 area 0.0.0.0 network 198.51.100.20 0.0.0.3 area 0.0.0.0 network 198.51.100.253 0.0.0.0 area 0.0.0.0 default-information originate ip route 0.0.0.0 0.0.0.0 GigabitEthernet1/0/20 203.0.113.249 name PE-RT01_WAN_Default_route ip route 198.51.100.0 255.255.255.0 Null0 254 name Aggregate_Routes ip route 198.51.100.240 255.255.255.248 Vlan10 198.51.100.6 name NAT-RT01_NAT_Pool ip route 198.51.100.240 255.255.255.248 Vlan11 198.51.100.14 5 name NAT-RT01_NAT_Pool |
ip routing
OSPF , PBR には有効化必須 router ospf L3SW01 と隣接関係を確立 デフォルトルート・Loopback・P2P アドレスを配布 L3SW のネットワークアドレスを受信する ip route PE-RT へのデフォルトルート、NAT-RT のグローバル アドレス プール宛のスタティックルートを設定する ip route Null0 LAN で使用するアドレスの集約ルート デフォルトルートで上位ルータとピンポン ルーティングループにならないように、自 LAN 管理のグローバル アドレスは Null0 宛集約ルートを設定する |
| アクセス リスト |
ip access-list extended ACL_NO_NAT 10 permit ip any 10.0.0.0 0.255.255.255 20 permit ip any 172.0.0.0 0.240.255.255 30 permit ip any 192.168.0.0 0.0.255.255 40 permit ip any 100.64.0.0 0.63.255.255 50 permit ip any 198.51.100.0 0.0.0.255 ip access-list extended ACL_NAT 10 permit ip 10.0.0.0 0.255.255.255 any 20 permit ip 172.0.0.0 0.240.255.255 any 30 permit ip 192.168.0.0 0.0.255.255 any 40 permit ip 100.64.0.0 0.63.255.255 any |
ip access-list extended ACL_NO_NAT
PBR させたくないトラフィックを定義する deny エントリは使用できない LAN アドレス宛のトラフィックを書くのが基本 ip access-list extended ACL_NAT NAT させたいトラフィックを定義する 送信元がプライベート IP や CGN 用のプロバイダー シェアードアドレスが送信元のトラフィックを書く |
| ルートマップ |
route-map RM_NAT_PBR deny 10 match ip address ACL_NO_NAT route-map RM_NAT_PBR permit 20 match ip address ACL_NAT set ip next-hop 198.51.100.10 198.51.100.18 |
route-map RM_NAT_PBR deny 10
ACL_NO_NAT に該当するトラフィックはシーケンス 20 に進まず、通常のルーティング処理を行う 該当しないトラフィックはシーケンス 20 に進む route-map RM_NAT_PBR permit 20 ACL_NAT に該当するトラフィックは、set ip next-hop の最初のアドレスへ転送する 最初のアドレスをと同一サブネットのインターフェースが存在しない or ダウンしている場合、2 つめの next-hop へ転送する 主に以下の場合は、同一サブネットのインターフェースがダウンしても、2 つめの next-hop に切り替わらない
|
| 種別 | L3SW01 コンフィグ | 解説 |
|---|---|---|
| インターフェース |
show configuration commands | match "eth|static|nat" set interfaces ethernet eth0 address '10.10.253.3/24' set interfaces ethernet eth0 description 'CE-RT01_Gi1/0/13' set interfaces ethernet eth0 hw-id '90:1b:0e:14:70:2c' set interfaces ethernet eth0 vif 10 address '198.51.100.6/30' set interfaces ethernet eth0 vif 10 description 'NAT_outside_Active' set interfaces ethernet eth0 vif 20 address '198.51.100.10/30' set interfaces ethernet eth0 vif 20 description 'NAT_inside_Active' set interfaces ethernet eth1 description 'CE-RT01_Gi1/0/14' set interfaces ethernet eth1 hw-id '00:0e:0c:d8:16:40' set interfaces ethernet eth1 vif 11 address '198.51.100.14/30' set interfaces ethernet eth1 vif 11 description 'NAT_outside_Standby' set interfaces ethernet eth1 vif 21 address '198.51.100.18/30' set interfaces ethernet eth1 vif 21 description 'NAT_inside_Standby' set interfaces ethernet eth1 vif 250 address '10.10.250.3/24' |
eth0
NAT outside を vif 10 , NAT inside を vif 20 に設定し、ワンアーム構成を取る eth1 eth0 ダウン時にフェイルオーバーできるように、eth1 にも同様の設定を行う |
| ルーティング |
set protocols static route 0.0.0.0/0 next-hop 198.51.100.5 set protocols static route 0.0.0.0/0 next-hop 198.51.100.13 distance '5' set protocols static route 10.0.0.0/8 next-hop 198.51.100.9 set protocols static route 10.0.0.0/8 next-hop 198.51.100.17 distance '5' set protocols static route 100.64.0.0/10 next-hop 198.51.100.9 set protocols static route 100.64.0.0/10 next-hop 198.51.100.17 distance '5' set protocols static route 172.16.0.0/12 next-hop 198.51.100.9 set protocols static route 172.16.0.0/12 next-hop 198.51.100.17 distance '5' set protocols static route 192.168.0.0/16 next-hop 198.51.100.9 set protocols static route 192.168.0.0/16 next-hop 198.51.100.17 distance '5' |
distance オプションなし
通常時に使用する、スタティック ルート distance 5 オプションあり eth0 障害時に使用する、フローティング スタティック ルート |
| NAT |
set nat source rule 10 description 'Exclude_VPN_Destination' set nat source rule 10 destination address '10.0.0.0/8' set nat source rule 10 exclude set nat source rule 10 outbound-interface 'eth0.10' set nat source rule 20 description 'Exclude_VPN_Destination' set nat source rule 20 destination address '172.16.0.0/12' set nat source rule 20 exclude set nat source rule 20 outbound-interface 'eth0.10' set nat source rule 30 description 'Exclude_VPN_Destination' set nat source rule 30 destination address '192.168.0.0/16' set nat source rule 30 exclude set nat source rule 30 outbound-interface 'eth0.10' set nat source rule 40 description 'Exclude_VPN_Destination' set nat source rule 40 destination address '100.64.0.0/10' set nat source rule 40 exclude set nat source rule 40 outbound-interface 'eth0.10' set nat source rule 50 description 'Exclude_VPN_Destination' set nat source rule 50 destination address '198.51.100.0/24' set nat source rule 50 exclude set nat source rule 50 outbound-interface 'eth0.10' set nat source rule 60 description 'Exclude_VPN_Destination' set nat source rule 60 destination address '10.0.0.0/8' set nat source rule 60 exclude set nat source rule 60 outbound-interface 'eth1.11' set nat source rule 70 description 'Exclude_VPN_Destination' set nat source rule 70 destination address '172.16.0.0/12' set nat source rule 70 exclude set nat source rule 70 outbound-interface 'eth1.11' set nat source rule 80 description 'Exclude_VPN_Destination' set nat source rule 80 destination address '192.168.0.0/16' set nat source rule 80 exclude set nat source rule 80 outbound-interface 'eth1.11' set nat source rule 90 description 'Exclude_VPN_Destination' set nat source rule 90 destination address '100.64.0.0/10' set nat source rule 90 exclude set nat source rule 90 outbound-interface 'eth1.11' set nat source rule 100 description 'Exclude_VPN_Destination' set nat source rule 100 destination address '198.51.100.0/24' set nat source rule 100 exclude set nat source rule 100 outbound-interface 'eth1.11' set nat source rule 110 description 'LAN_to_WAN_NAT' set nat source rule 110 outbound-interface 'eth0.10' set nat source rule 110 source address '10.0.0.0/8' set nat source rule 110 translation address '198.51.100.241' set nat source rule 120 description 'LAN_to_WAN_NAT' set nat source rule 120 outbound-interface 'eth0.10' set nat source rule 120 source address '172.16.0.0/12' set nat source rule 120 translation address '198.51.100.242' set nat source rule 130 description 'LAN_to_WAN_NAT' set nat source rule 130 outbound-interface 'eth0.10' set nat source rule 130 source address '192.168.0.0/16' set nat source rule 130 translation address '198.51.100.243' set nat source rule 140 description 'LAN_to_WAN_NAT' set nat source rule 140 outbound-interface 'eth0.10' set nat source rule 140 source address '100.64.0.0/10' set nat source rule 140 translation address '198.51.100.244' set nat source rule 210 description 'LAN_to_WAN_NAT' set nat source rule 210 outbound-interface 'eth1.11' set nat source rule 210 source address '10.0.0.0/8' set nat source rule 210 translation address '198.51.100.241' set nat source rule 220 description 'LAN_to_WAN_NAT' set nat source rule 220 outbound-interface 'eth1.11' set nat source rule 220 source address '172.16.0.0/12' set nat source rule 220 translation address '198.51.100.242' set nat source rule 230 description 'LAN_to_WAN_NAT' set nat source rule 230 outbound-interface 'eth1.11' set nat source rule 230 source address '192.168.0.0/16' set nat source rule 230 translation address '198.51.100.243' set nat source rule 240 description 'LAN_to_WAN_NAT' set nat source rule 240 outbound-interface 'eth1.11' set nat source rule 240 source address '100.64.0.0/10' set nat source rule 240 translation address '198.51.100.244' |
rule 10 - 100
宛先が LAN アドレスの場合は NAT から除外する rule 110 - 240 宛先が WAN アドレスの場合は NAT する |
| 種別 | L3SW01 コンフィグ | 解説 |
|---|---|---|
| インターフェース |
show run | s ip routing|1/0/23|ip route [0-9]|router|Loopback interface Loopback0 description Router-ID ip address 198.51.100.252 255.255.255.255 interface Loopback1 description Global_source ip address 198.51.100.251 255.255.255.255 interface Loopback2 description Private_source1 ip address 10.0.0.1 255.255.255.0 interface GigabitEthernet1/0/23 description L3SW01_Gi1/0/1 no switchport ip address 198.51.100.22 255.255.255.252 ip ospf network point-to-point |
Loopback1
NAT されない場合の挙動を確認するため、ping 送信元用に Loopback1 を設定する Loopback2 NAT される場合の挙動を確認するため、ping 送信元用に Loopback1 を設定する |
| ルーティング |
ip routing router ospf 1 router-id 198.51.100.252 passive-interface default no passive-interface GigabitEthernet1/0/23 network 10.0.0.0 0.0.0.255 area 0.0.0.0 network 172.16.0.0 0.0.0.255 area 0.0.0.0 network 198.51.100.20 0.0.0.3 area 0.0.0.0 network 198.51.100.251 0.0.0.0 area 0.0.0.0 network 198.51.100.252 0.0.0.0 area 0.0.0.0 |
ip routing
OSPF には有効化必須 router ospf CE-RT01 と隣接関係を確立 デフォルトルート・Loopback・P2P アドレスを配布 CE-RT01 のネットワークアドレス・デフォルトルートを受信する |
疎通確認
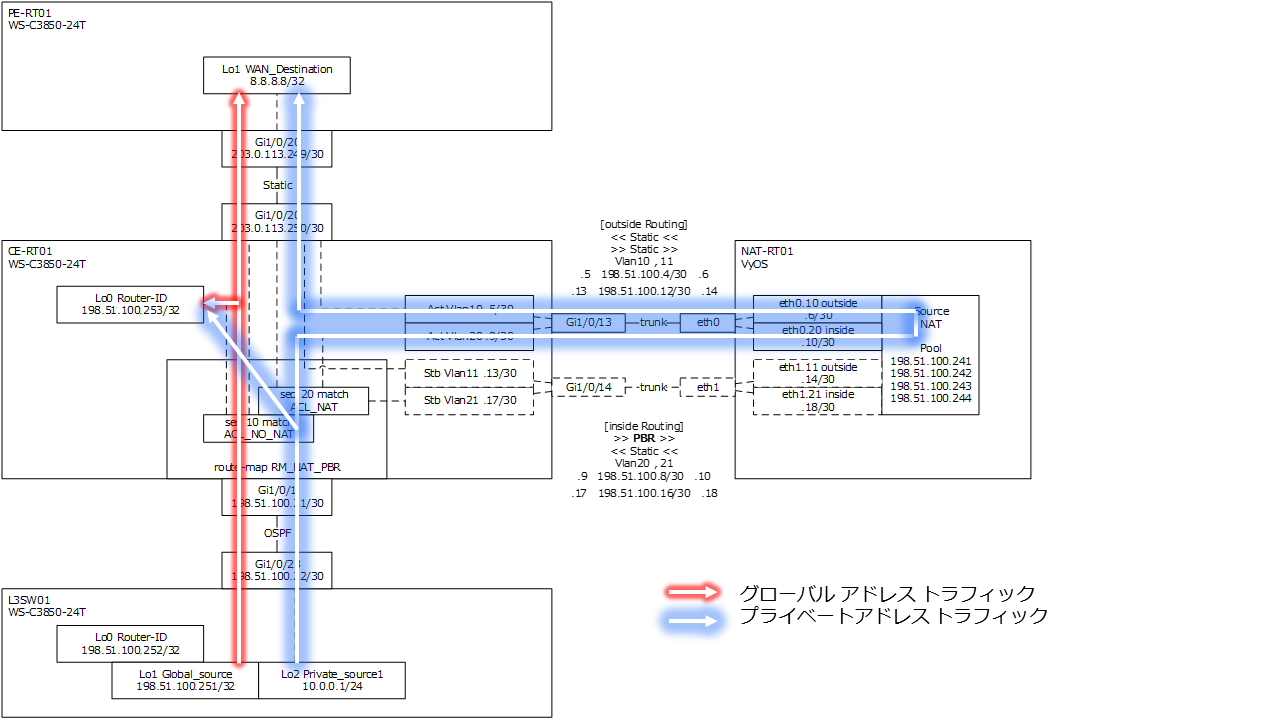
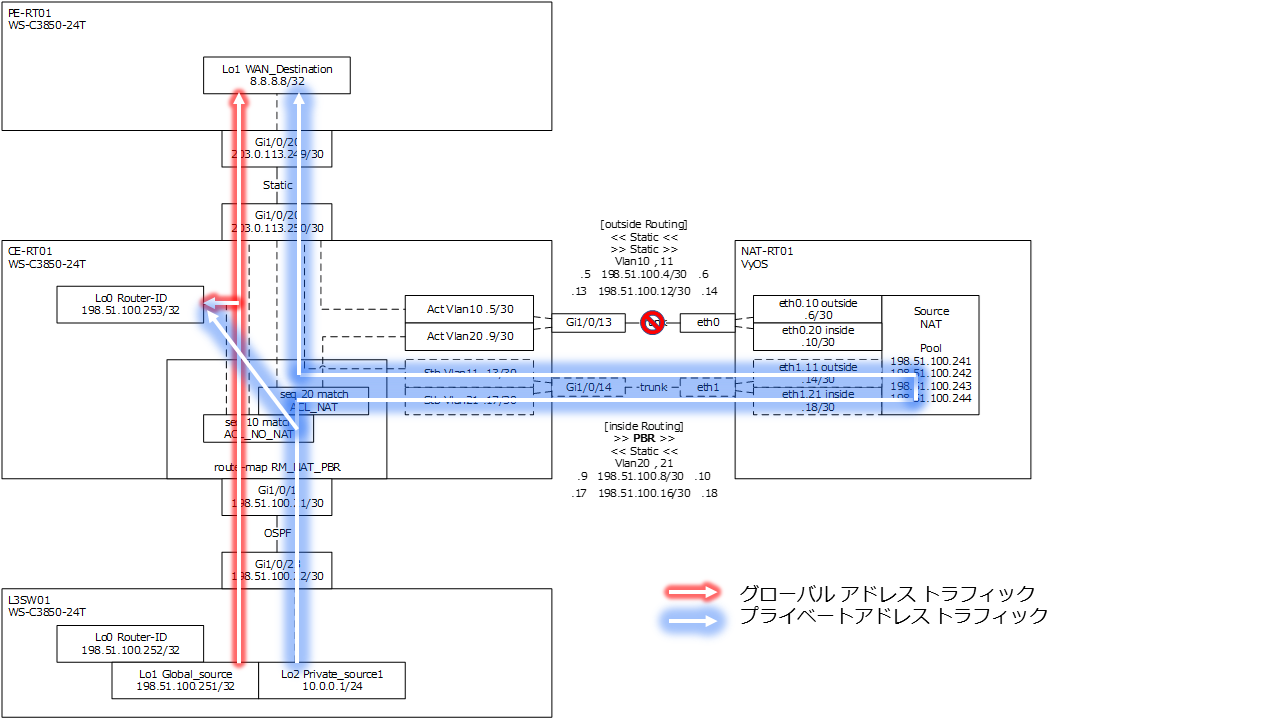
| 確認 | L3SW01 送信元グローバル アドレス | L3SW01 送信元プライベート アドレス | 備考 |
|---|---|---|---|
| 疎通確認 |
L3SW01(tcl)#### L3SW01
L3SW01(tcl)#!!! Success is OK
L3SW01(tcl)#tclsh
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { ping $address source Lo1 }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 203.0.113.249, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 203.0.113.250, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.253, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.5, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.6, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.9, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.10, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.13, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.14, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.17, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.18, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.21, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/7 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.22, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.252, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.251
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/6 ms
L3SW01(tcl)#
|
L3SW01(tcl)#tclsh
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { ping $address source Lo2 }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 203.0.113.249, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 203.0.113.250, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.253, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.5, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.6, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.9, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.10, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.13, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.14, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.17, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.18, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.21, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.22, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/2 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 198.51.100.252, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/2 ms
L3SW01(tcl)#
|
経路確認
| 確認 | L3SW01 送信元グローバル アドレス | L3SW01 送信元プライベート アドレス | 備考 |
|---|---|---|---|
| 通常時
経路確認 |
L3SW01(tcl)#tclsh
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { traceroute $address source Lo1 }
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 2 msec 3 msec
2 203.0.113.249 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 203.0.113.249
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 *
203.0.113.249 3 msec *
Type escape sequence to abort.
Tracing the route to 203.0.113.250
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.253
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 4 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.5
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 4 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.6
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.6 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.9
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 4 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.10
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.10 2 msec 2 msec 1 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.13
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 4 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.14
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 198.51.100.14 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.17
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.18
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 4 msec 2 msec 3 msec
2 198.51.100.18 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.21
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.22
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.22 3 msec * 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.252
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.252 2 msec * 2 msec
L3SW01(tcl)#
|
L3SW01(tcl)#tclsh
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { traceroute $address source Lo2 }
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 198.51.100.10 1 msec 2 msec 2 msec
3 198.51.100.5 3 msec 3 msec 3 msec
4 203.0.113.249 3 msec * 4 msec
Type escape sequence to abort.
Tracing the route to 203.0.113.249
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 198.51.100.10 1 msec 2 msec 2 msec
3 198.51.100.5 3 msec 3 msec 3 msec
4 *
203.0.113.249 4 msec *
Type escape sequence to abort.
Tracing the route to 203.0.113.250
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.10 2 msec 3 msec 1 msec
3 198.51.100.5 3 msec * 4 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.253
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.5
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.6
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 4 msec
2 198.51.100.6 2 msec 3 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.9
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.10
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.10 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.13
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.14
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.14 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.17
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.18
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 13 msec 3 msec 2 msec
2 198.51.100.18 1 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.21
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.22
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.22 3 msec * 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.252
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.252 2 msec * 2 msec
L3SW01(tcl)#
|
|
| PBR next-hop 1 つめ
障害時 経路確認 |
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { traceroute $address source Lo1 }
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 2 msec 2 msec
2 203.0.113.249 3 msec * 2 msec
Type escape sequence to abort.
Tracing the route to 203.0.113.249
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 2 msec 3 msec
2 *
203.0.113.249 3 msec *
Type escape sequence to abort.
Tracing the route to 203.0.113.250
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 5 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.253
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.5
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2 * *
Type escape sequence to abort.
Tracing the route to 198.51.100.6
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2
Type escape sequence to abort.
Tracing the route to 198.51.100.9
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2
Type escape sequence to abort.
Tracing the route to 198.51.100.10
VRF info: (vrf in name/id, vrf out name/id)
1 * *
Type escape sequence to abort.
Tracing the route to 198.51.100.13
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 4 msec * 4 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.14
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 3 msec
2 198.51.100.14 2 msec 2 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.17
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.18
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 198.51.100.18 1 msec 3 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.21
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.22
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.22 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.252
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.252 2 msec * 2 msec
L3SW01(tcl)#
|
L3SW01(tcl)#tclsh
L3SW01(tcl)#foreach address {
+> 8.8.8.8
+> 203.0.113.249
+> 203.0.113.250
+> 198.51.100.253
+> 198.51.100.5
+> 198.51.100.6
+> 198.51.100.9
+> 198.51.100.10
+> 198.51.100.13
+> 198.51.100.14
+> 198.51.100.17
+> 198.51.100.18
+> 198.51.100.21
+> 198.51.100.22
+> 198.51.100.252
+>} { traceroute $address source Lo2 }
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 2 msec
2 198.51.100.18 2 msec 2 msec 2 msec
3 198.51.100.13 2 msec 2 msec 2 msec
4 203.0.113.249 3 msec * 4 msec
Type escape sequence to abort.
Tracing the route to 203.0.113.249
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 2 msec 2 msec
2 198.51.100.18 2 msec 2 msec 2 msec
3 198.51.100.13 2 msec 3 msec 4 msec
4 *
203.0.113.249 4 msec *
Type escape sequence to abort.
Tracing the route to 203.0.113.250
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 3 msec 6 msec
2 198.51.100.18 2 msec 3 msec 2 msec
3 198.51.100.13 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.253
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 2 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.5
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2
Type escape sequence to abort.
Tracing the route to 198.51.100.6
VRF info: (vrf in name/id, vrf out name/id)
1 * *
Type escape sequence to abort.
Tracing the route to 198.51.100.9
VRF info: (vrf in name/id, vrf out name/id)
1 * *
Type escape sequence to abort.
Tracing the route to 198.51.100.10
VRF info: (vrf in name/id, vrf out name/id)
1 * * *
2
Type escape sequence to abort.
Tracing the route to 198.51.100.13
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 4 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.14
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec 2 msec 3 msec
2 198.51.100.14 2 msec 1 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.17
VRF info: (vrf in name/id, vrf out name/id)
1 *
198.51.100.21 3 msec *
Type escape sequence to abort.
Tracing the route to 198.51.100.18
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 4 msec 3 msec 2 msec
2 198.51.100.18 2 msec 3 msec 2 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.21
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.21 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.22
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.22 3 msec * 3 msec
Type escape sequence to abort.
Tracing the route to 198.51.100.252
VRF info: (vrf in name/id, vrf out name/id)
1 198.51.100.252 2 msec * 2 msec
L3SW01(tcl)#
|
エントリ確認
| プロトコル | CE-RT01 通常時 | CE-RT01 Gi1/0/13 障害時` | 備考 |
|---|---|---|---|
| PBR |
CE-RT01(config-if)#do sh run | s route-map
ip policy route-map RM_NAT_PBR
route-map RM_NAT_PBR deny 10
match ip address ACL_NO_NAT
route-map RM_NAT_PBR permit 20
match ip address ACL_NAT
set ip next-hop 198.51.100.10 198.51.100.18
CE-RT01(config-if)#do sh ip route 198.51.100.10 255.255.255.252
Load for five secs: 5%/0%; one minute: 5%; five minutes: 5%
Time source is NTP, 15:54:08.189 JST Wed Sep 25 2024
Routing entry for 198.51.100.8/30
Known via "connected", distance 0, metric 0 (connected, via interface)
Routing Descriptor Blocks:
* directly connected, via Vlan20
Route metric is 0, traffic share count is 1
CE-RT01(config-if)#do sh ip route 198.51.100.18
Load for five secs: 7%/0%; one minute: 5%; five minutes: 6%
Time source is NTP, 15:38:42.872 JST Wed Sep 25 2024
Routing entry for 198.51.100.16/30
Known via "connected", distance 0, metric 0 (connected, via interface)
Routing Descriptor Blocks:
* directly connected, via Vlan21
Route metric is 0, traffic share count is 1
CE-RT01(config-if)#
|
CE-RT01(config-if)#do sh run | s route-map
ip policy route-map RM_NAT_PBR
route-map RM_NAT_PBR deny 10
match ip address ACL_NO_NAT
route-map RM_NAT_PBR permit 20
match ip address ACL_NAT
set ip next-hop 198.51.100.10 198.51.100.18
CE-RT01(config-if)#do sh ip route 198.51.100.10 255.255.255.252
Load for five secs: 4%/0%; one minute: 6%; five minutes: 5%
Time source is NTP, 15:52:51.641 JST Wed Sep 25 2024
% Subnet not in table
CE-RT01(config-if)#
CE-RT01(config-if)#do sh ip route 198.51.100.18
Load for five secs: 5%/0%; one minute: 5%; five minutes: 6%
Time source is NTP, 15:39:33.129 JST Wed Sep 25 2024
Routing entry for 198.51.100.16/30
Known via "connected", distance 0, metric 0 (connected, via interface)
Routing Descriptor Blocks:
* directly connected, via Vlan21
Route metric is 0, traffic share count is 1
|
PBR の next-hop 切替時は、障害が発生した direct connect の L3 インターフェースがダウンしており、該当のコネクテッド ルートが存在しなくなる必要がある |
| スタティック ルーティング |
CE-RT01(config-if)#do sh run | in ip route [0-9].*6 name ip route 198.51.100.240 255.255.255.248 Vlan10 198.51.100.6 name NAT-RT01_NAT_Pool CE-RT01(config-if)#do sh ip route 198.51.100.240 255.255.255.248
Load for five secs: 5%/0%; one minute: 7%; five minutes: 6%
Time source is NTP, 15:37:27.052 JST Wed Sep 25 2024
Routing entry for 198.51.100.240/29
Known via "static", distance 1, metric 0
Routing Descriptor Blocks:
* 198.51.100.6, via Vlan10
Route metric is 0, traffic share count is 1
|
CE-RT01(config-if)#do sh run | in ip route [0-9].*5 name ip route 198.51.100.240 255.255.255.248 Vlan11 198.51.100.14 5 name NAT-RT01_NAT_Pool CE-RT01(config-if)#do sh ip route 198.51.100.240 255.255.255.248
Load for five secs: 7%/0%; one minute: 6%; five minutes: 6%
Time source is NTP, 15:37:48.825 JST Wed Sep 25 2024
Routing entry for 198.51.100.240/29
Known via "static", distance 5, metric 0
Routing Descriptor Blocks:
* 198.51.100.14, via Vlan11
Route metric is 0, traffic share count is 1
|
NAT-RT01 グローバル アドレス プール宛スタティックルートが障害切り替えされている |
動作確認 - ホスト別コマンドリスト
PBR は設定した機器で動作確認するコマンドがほぼ存在しない。
- ACL カウンターは動作しない
- show route-map のカウンタもハードウェア転送では動作しない
- 一応 ip local policy route-map で動作確認することは可能
- 下手な設定をすると OSPF がダウンしたりするため、少なくとも商用機ではやらない方が良い
このため、下位側の機器で ping / traceroute を実施するのが動作確認としてマストとなる。
CE-RT01
- show ip policy
L3SW01
- ping
- traceroute
リファレンス
Cisco
IP Routing Configuration Guide, Cisco IOS XE Gibraltar 16.12.x (Catalyst 3850 Switches)
脚注
- ↑ 1.0 1.1 How to Configure PBR ip next-hop recursive and ip next-hop verify availability features are not available and the next-hop should be directly connected.