2024-06-16 vJunos-switch BGP-EVPN-VXLAN 機能検証
先日リリースされた vJunos-switch について、BGP EVPN VXLAN の検証を実施しました。
このページにラボシナリオとして、コンフィグや確認コマンド、疎通確認のポイントなどをまとめています。
目的
レイヤ 3 インターフェース経由で、同一サブネットの通信が可能であること。
host#1 --- vEX#1 --- Routing --- vEX#2 --- host#2
192.168.0.1 192.168.0.2
検証環境
EVE-NG Community Edition
Juniper vJunos-switch 23.2R1.14
Cisco CSR1000V 17.3.4a
構成図
- CSR1000V : CSR01,02
- vJunos-switch : vEX01,02
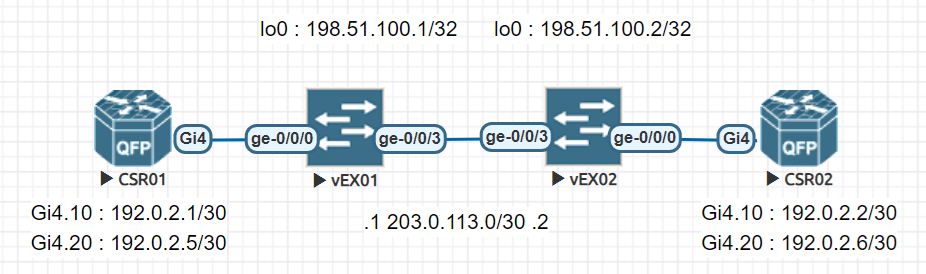
vEX 間はルーティングを動作させて、CSR01 , 02 間で同一セグメント内の通信可否を確認します。
IP アドレッシング
| 文書用例示アドレス | |||||
|---|---|---|---|---|---|
| 種別 | ネットワーク アドレス | ホスト | インターフェース | ホスト アドレス | 備考 |
| グローバルアドレス | 203.0.113.0/30 | vEX01 | ge-0/0/3.0 | 203.0.113.1/30 | |
| vEX02 | ge-0/0/3.0 | 203.0.113.2/30 | |||
| 198.51.100.0/24 | vEX01 | lo0.0 | 198.51.100.1/32 | ||
| vEX02 | 198.51.100.1/32 | 198.51.100.2/32 | |||
| プライベートアドレス | 192.0.2.0/24 | CSR01 | Gi4.10 | 192.0.2.1/30 | |
| Gi4.20 | 192.0.2.5/30 | ||||
| CSR02 | Gi4.10 | 192.0.2.2/30 | |||
| Gi4.20 | 192.0.2.6/30 | ||||
コンフィギュレーション
ここではプロトコル・ホスト別にコンフィギュレーションを簡単に解説します。
自分でコンフィグを組んでみたい人向けに、デフォルトでは表示しません。
このページのリファレンスに記載した、Juniper や日商エレのサイトを参考に設定してみると良いでしょう。
CSR01 , 02
| プロトコル | CSR01 コンフィグ | CSR02 コンフィグ | 解説 |
|---|---|---|---|
| IPv4 |
CSR01#show run | s net4 interface GigabitEthernet4 description vEX01_ge-0/0/0 no ip address negotiation auto no mop enabled no mop sysid interface GigabitEthernet4.10 encapsulation dot1Q 10 ip address 192.0.2.1 255.255.255.252 interface GigabitEthernet4.20 encapsulation dot1Q 20 ip address 192.0.2.5 255.255.255.252 |
CSR02#show run | s net4 interface GigabitEthernet4 description vEX02_ge-0/0/0 no ip address negotiation auto no mop enabled no mop sysid interface GigabitEthernet4.10 encapsulation dot1Q 10 ip address 192.0.2.2 255.255.255.252 interface GigabitEthernet4.20 encapsulation dot1Q 20 ip address 192.0.2.6 255.255.255.252 |
vEX01 , 02
| プロトコル | vEX01 コンフィグ | vEX01 コンフィグ | 解説 |
|---|---|---|---|
| インターフェース
(ユーザポート) |
interfaces {
ge-0/0/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
unit 10 {
family ethernet-switching {
interface-mode trunk;
vlan {
members v10;
}
}
}
unit 20 {
family ethernet-switching {
interface-mode trunk;
vlan {
members v20;
}
}
}
}
}
|
interfaces {
ge-0/0/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
unit 10 {
family ethernet-switching {
interface-mode trunk;
vlan {
members v10;
}
}
}
unit 20 {
family ethernet-switching {
interface-mode trunk;
vlan {
members v20;
}
}
}
}
}
|
ユーザ収容ポート
通常の trunk 設定に加えて、flexible-vlan tagging と flexible-ethernet-services を設定する |
| インターフェース
(ネットワークポート) |
interfaces {
ge-0/0/3 {
unit 0 {
family inet {
address 203.0.113.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 198.51.100.1/32;
}
}
}
}
|
interfaces {
ge-0/0/3 {
unit 0 {
family inet {
address 203.0.113.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 198.51.100.2/32;
}
}
}
}
|
OSPF 接続用 |
| ルーティング
インスタンス |
routing-instances {
EVPN-1 {
instance-type mac-vrf;
protocols {
evpn {
encapsulation vxlan;
extended-vni-list all;
}
}
vtep-source-interface lo0.0;
service-type vlan-based;
interface ge-0/0/0.10;
route-distinguisher 198.51.100.1:1;
vrf-target target:65000:1;
vlans {
v10 {
vlan-id 10;
##
## Warning: requires 'vxlan' license
##
vxlan {
vni 100010;
}
}
}
}
EVPN-2 {
instance-type mac-vrf;
protocols {
evpn {
encapsulation vxlan;
extended-vni-list all;
}
}
vtep-source-interface lo0.0;
service-type vlan-based;
interface ge-0/0/0.20;
route-distinguisher 198.51.100.1:1;
vrf-target target:65000:1;
vlans {
v20 {
vlan-id 20;
##
## Warning: requires 'vxlan' license
##
vxlan {
vni 100020;
}
}
}
}
}
|
routing-instances {
EVPN-1 {
instance-type mac-vrf;
protocols {
evpn {
encapsulation vxlan;
extended-vni-list all;
}
}
vtep-source-interface lo0.0;
service-type vlan-based;
interface ge-0/0/0.10;
route-distinguisher 198.51.100.1:1;
vrf-target target:65000:1;
vlans {
v10 {
vlan-id 10;
##
## Warning: requires 'vxlan' license
##
vxlan {
vni 100010;
}
}
}
}
EVPN-2 {
instance-type mac-vrf;
protocols {
evpn {
encapsulation vxlan;
extended-vni-list all;
}
}
vtep-source-interface lo0.0;
service-type vlan-based;
interface ge-0/0/0.20;
route-distinguisher 198.51.100.2:1;
vrf-target target:65000:1;
vlans {
v20 {
vlan-id 20;
##
## Warning: requires 'vxlan' license
##
vxlan {
vni 100020;
}
}
}
}
}
|
instance-type mac-vrf
インスタンスの種類を設定
EVPN を設定
protocols evpn encapsulation vxlan カプセル化方式を設定
通す VNI を設定
VXLAN Tunnel Endpoint を lo0.0 に設定 トラフィックはこのインターフェースを通るため、lo0.0 同士の疎通が通っていないとサービスが止まる
このインスタンスに属するインターフェースを設定
route-distinguisher 198.51.100.2:1 VRF 識別子の RD を設定
VRF のルートターゲットを設定
dot1q タグを 10 に指定
VNI を 100010 に指定 vlan-id と同一の階層にあるため、vlan-id 10 と紐づくことになる |
| ルーティング
オプション |
routing-options {
router-id 198.51.100.1;
autonomous-system 65000;
}
|
routing-options {
router-id 198.51.100.2;
autonomous-system 65000;
}
|
BGP ルータ ID と AS 番号を指定 |
| OSPF |
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/3.0 {
interface-type p2p;
}
interface lo0.0;
}
}
}
|
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/3.0 {
interface-type p2p;
}
interface lo0.0;
}
}
}
|
OSPF エリア 0.0.0.0 に属するインターフェースを指定 |
| BGP |
protocols {
##
## Warning: requires 'bgp' license
##
bgp {
group ibgp {
type internal;
local-address 198.51.100.1;
family evpn {
signaling;
}
neighbor 198.51.100.2;
}
}
}
|
protocols {
##
## Warning: requires 'bgp' license
##
bgp {
group ibgp {
type internal;
local-address 198.51.100.2;
family evpn {
signaling;
}
neighbor 198.51.100.1;
}
}
}
|
BGP を設定
ピアリングに使うアドレスを lo0 として、OSPF が Up して (アンダーレイ) lo0 アドレスを交換したあとに BGP のピアが Up する (オーバーレイ) ようにしている
BGP でやり取りする情報に EVPN を設定 VXLAN の場合 MAC アドレスなどがやり取りされる |
| 種別 | vEX01 set コンフィグ | vEX02 set コンフィグ | 解説 |
|---|---|---|---|
| インターフェース |
set interfaces ge-0/0/0 flexible-vlan-tagging set interfaces ge-0/0/0 encapsulation flexible-ethernet-services set interfaces ge-0/0/0 unit 10 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 10 family ethernet-switching vlan members v10 set interfaces ge-0/0/0 unit 20 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 20 family ethernet-switching vlan members v20 set interfaces ge-0/0/3 unit 0 family inet address 203.0.113.1/30 |
set interfaces ge-0/0/0 flexible-vlan-tagging set interfaces ge-0/0/0 encapsulation flexible-ethernet-services set interfaces ge-0/0/0 unit 10 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 10 family ethernet-switching vlan members v10 set interfaces ge-0/0/0 unit 20 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 20 family ethernet-switching vlan members v20 set interfaces ge-0/0/3 unit 0 family inet address 203.0.113.2/30 |
|
| ルーティング
インスタンス |
set routing-instances EVPN-1 instance-type mac-vrf set routing-instances EVPN-1 protocols evpn encapsulation vxlan set routing-instances EVPN-1 protocols evpn extended-vni-list all set routing-instances EVPN-1 vtep-source-interface lo0.0 set routing-instances EVPN-1 service-type vlan-based set routing-instances EVPN-1 interface ge-0/0/0.10 set routing-instances EVPN-1 route-distinguisher 198.51.100.1:1 set routing-instances EVPN-1 vrf-target target:65000:1 set routing-instances EVPN-1 vlans v10 vlan-id 10 set routing-instances EVPN-1 vlans v10 vxlan vni 100010 set routing-instances EVPN-2 instance-type mac-vrf set routing-instances EVPN-2 protocols evpn encapsulation vxlan set routing-instances EVPN-2 protocols evpn extended-vni-list all set routing-instances EVPN-2 vtep-source-interface lo0.0 set routing-instances EVPN-2 service-type vlan-based set routing-instances EVPN-2 interface ge-0/0/0.20 set routing-instances EVPN-2 route-distinguisher 198.51.100.1:1 set routing-instances EVPN-2 vrf-target target:65000:1 set routing-instances EVPN-2 vlans v20 vlan-id 20 set routing-instances EVPN-2 vlans v20 vxlan vni 100020 |
set routing-instances EVPN-1 instance-type mac-vrf set routing-instances EVPN-1 protocols evpn encapsulation vxlan set routing-instances EVPN-1 protocols evpn extended-vni-list all set routing-instances EVPN-1 vtep-source-interface lo0.0 set routing-instances EVPN-1 service-type vlan-based set routing-instances EVPN-1 interface ge-0/0/0.10 set routing-instances EVPN-1 route-distinguisher 198.51.100.2:1 set routing-instances EVPN-1 vrf-target target:65000:1 set routing-instances EVPN-1 vlans v10 vlan-id 10 set routing-instances EVPN-1 vlans v10 vxlan vni 100010 set routing-instances EVPN-2 instance-type mac-vrf set routing-instances EVPN-2 protocols evpn encapsulation vxlan set routing-instances EVPN-2 protocols evpn extended-vni-list all set routing-instances EVPN-2 vtep-source-interface lo0.0 set routing-instances EVPN-2 service-type vlan-based set routing-instances EVPN-2 interface ge-0/0/0.20 set routing-instances EVPN-2 route-distinguisher 198.51.100.2:1 set routing-instances EVPN-2 vrf-target target:65000:1 set routing-instances EVPN-2 vlans v20 vlan-id 20 set routing-instances EVPN-2 vlans v20 vxlan vni 100020 |
|
| ルーティング
オプション |
set routing-options router-id 198.51.100.1 set routing-options autonomous-system 65000 |
set routing-options router-id 198.51.100.2 set routing-options autonomous-system 65000 |
|
| OSPF |
set protocols ospf area 0.0.0.0 interface ge-0/0/3.0 interface-type p2p set protocols ospf area 0.0.0.0 interface lo0.0 |
set protocols ospf area 0.0.0.0 interface ge-0/0/3.0 interface-type p2p set protocols ospf area 0.0.0.0 interface lo0.0 |
|
| BGP |
set protocols bgp group ibgp type internal set protocols bgp group ibgp local-address 198.51.100.1 set protocols bgp group ibgp family evpn signaling set protocols bgp group ibgp neighbor 198.51.100.2 |
set protocols bgp group ibgp type internal set protocols bgp group ibgp local-address 198.51.100.2 set protocols bgp group ibgp family evpn signaling set protocols bgp group ibgp neighbor 198.51.100.1 |
疎通確認
| 確認 | CSR01 | CSR02 | 備考 |
|---|---|---|---|
| 疎通確認 |
CSR01#ping 192.0.2.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.0.2.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/5 ms CSR01# CSR01#traceroute 192.0.2.2 Type escape sequence to abort. Tracing the route to 192.0.2.2 VRF info: (vrf in name/id, vrf out name/id) 1 192.0.2.2 25 msec * 4 msec CSR01# CSR01#ping 192.0.2.6 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.0.2.6, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/5 ms CSR01# CSR01#traceroute 192.0.2.6 Type escape sequence to abort. Tracing the route to 192.0.2.6 VRF info: (vrf in name/id, vrf out name/id) 1 192.0.2.6 5 msec * 5 msec CSR01# CSR01#show ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.0.2.1 - 5000.0003.0003 ARPA GigabitEthernet4.10 Internet 192.0.2.2 91 5000.0004.0003 ARPA GigabitEthernet4.10 Internet 192.0.2.5 - 5000.0003.0003 ARPA GigabitEthernet4.20 Internet 192.0.2.6 91 5000.0004.0003 ARPA GigabitEthernet4.20 |
CSR02#ping 192.0.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.0.2.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/4 ms CSR02# CSR02#traceroute 192.0.2.1 Type escape sequence to abort. Tracing the route to 192.0.2.1 VRF info: (vrf in name/id, vrf out name/id) 1 192.0.2.1 65 msec * 4 msec CSR02# CSR02#ping 192.0.2.5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.0.2.5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms CSR02# CSR02#traceroute 192.0.2.5 Type escape sequence to abort. Tracing the route to 192.0.2.5 VRF info: (vrf in name/id, vrf out name/id) 1 192.0.2.5 4 msec * 4 msec CSR02# CSR02#show ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.0.2.1 109 5000.0003.0003 ARPA GigabitEthernet4.10 Internet 192.0.2.2 - 5000.0004.0003 ARPA GigabitEthernet4.10 Internet 192.0.2.5 109 5000.0003.0003 ARPA GigabitEthernet4.20 Internet 192.0.2.6 - 5000.0004.0003 ARPA GigabitEthernet4.20 |
アンダーレイ・オーバーレイ動作確認
| プロトコル | CSR01 | CSR02 | 備考 |
|---|---|---|---|
| OSPF
アンダーレイ |
root@vEX01> show ospf neighbor Address Interface State ID Pri Dead 203.0.113.2 ge-0/0/3.0 Full 198.51.100.2 128 32 root@vEX01> |
root@vEX02> show ospf neighbor Address Interface State ID Pri Dead 203.0.113.1 ge-0/0/3.0 Full 198.51.100.1 128 35 root@vEX02> |
OSPF が Full になっていること |
| BGP
オーバーレイ |
root@vEX01> show bgp summary
Warning: License key missing; requires 'bgp' license
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 1 Peers: 1 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
bgp.evpn.0
2 2 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
198.51.100.2 65000 332 332 0 0 2:21:58 Establ
bgp.evpn.0: 2/2/2/0
EVPN-1.evpn.0: 2/2/2/0
__default_evpn__.evpn.0: 0/0/0/0
EVPN-2.evpn.0: 2/2/2/0
root@vEX01>
|
root@vEX02> show bgp summary
Warning: License key missing; requires 'bgp' license
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 1 Peers: 1 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
bgp.evpn.0
2 2 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
198.51.100.1 65000 331 328 0 0 2:21:27 Establ
bgp.evpn.0: 2/2/2/0
EVPN-1.evpn.0: 2/2/2/0
__default_evpn__.evpn.0: 0/0/0/0
EVPN-2.evpn.0: 2/2/2/0
root@vEX02>
|
State が Establish で EVPN ルートを受信していること |
エントリ確認
| プロトコル | CSR01 | CSR02 | 備考 |
|---|---|---|---|
| OSPF |
root@vEX01> show route protocol ospf
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
+ = Active Route, - = Last Active, * = Both
198.51.100.2/32 *[OSPF/10] 02:27:46, metric 1
> to 203.0.113.2 via ge-0/0/3.0
224.0.0.5/32 *[OSPF/10] 03:50:32, metric 1
MultiRecv
inet6.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
bgp.evpn.0: 8 destinations, 8 routes (8 active, 0 holddown, 0 hidden)
EVPN-1.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
EVPN-2.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
root@vEX01>
|
root@vEX02> show route protocol ospf
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
+ = Active Route, - = Last Active, * = Both
198.51.100.1/32 *[OSPF/10] 02:28:25, metric 1
> to 203.0.113.1 via ge-0/0/3.0
224.0.0.5/32 *[OSPF/10] 03:51:04, metric 1
MultiRecv
inet6.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
bgp.evpn.0: 8 destinations, 8 routes (8 active, 0 holddown, 0 hidden)
EVPN-1.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
EVPN-2.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
root@vEX02>
|
OSPF はアンダーレイで動作するため、対向側 lo0 のアドレスを受信しているか確認します |
| BGP |
root@vEX01> show route protocol bgp
Warning: License key missing; requires 'bgp' license
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
inet6.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
bgp.evpn.0: 8 destinations, 8 routes (8 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:14, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:12, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.2/248 IM
*[BGP/170] 02:15:23, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.2/248 IM
*[BGP/170] 01:43:11, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
EVPN-1.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:14, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:12, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.2/248 IM
*[BGP/170] 02:15:23, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.2/248 IM
*[BGP/170] 01:43:11, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
EVPN-2.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:14, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:04:00:03/304 MAC/IP
*[BGP/170] 00:01:12, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.2/248 IM
*[BGP/170] 01:44:59, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.2/248 IM
*[BGP/170] 01:43:11, localpref 100, from 198.51.100.2
AS path: I, validation-state: unverified
> to 203.0.113.2 via ge-0/0/3.0
root@vEX01>
|
root@vEX02> show route protocol bgp
Warning: License key missing; requires 'bgp' license
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
inet6.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden)
Limit/Threshold: 1048576/1048576 destinations
bgp.evpn.0: 8 destinations, 8 routes (8 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:06, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:04, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.1/248 IM
*[BGP/170] 02:14:15, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.1/248 IM
*[BGP/170] 01:43:49, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
EVPN-1.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:06, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:04, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.1/248 IM
*[BGP/170] 02:14:15, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.1/248 IM
*[BGP/170] 01:43:49, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
EVPN-2.evpn.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:198.51.100.1:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:06, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6250
2:203.0.113.255:1::0::50:00:00:03:00:03/304 MAC/IP
*[BGP/170] 00:00:04, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0, Push 6251
3:198.51.100.1:1::0::198.51.100.1/248 IM
*[BGP/170] 01:42:05, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
3:203.0.113.255:1::0::198.51.100.1/248 IM
*[BGP/170] 01:42:05, localpref 100, from 198.51.100.1
AS path: I, validation-state: unverified
> to 203.0.113.1 via ge-0/0/3.0
root@vEX02>
|
BGP はオーバーレイとして、対向側の MAC アドレスを受信しているか確認します |
| MAC |
root@vEX01> show ethernet-switching table
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC,
B - Blocked MAC)
Ethernet switching table : 2 entries, 2 learned
Routing instance : EVPN-1
Vlan MAC MAC GBP Logical SVLBNH/ Active
name address flags tag interface VENH Index source
v10 50:00:00:03:00:03 D ge-0/0/0.10
v10 50:00:00:04:00:03 DR vtep.32768 198.51.100.2
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC,
B - Blocked MAC)
Ethernet switching table : 2 entries, 2 learned
Routing instance : EVPN-2
Vlan MAC MAC GBP Logical SVLBNH/ Active
name address flags tag interface VENH Index source
v20 50:00:00:03:00:03 D ge-0/0/0.20
v20 50:00:00:04:00:03 DR vtep.32772 198.51.100.2
root@vEX01>
|
root@vEX02> show ethernet-switching table
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC,
B - Blocked MAC)
Ethernet switching table : 2 entries, 2 learned
Routing instance : EVPN-1
Vlan MAC MAC GBP Logical SVLBNH/ Active
name address flags tag interface VENH Index source
v10 50:00:00:03:00:03 DR vtep.32768 198.51.100.1
v10 50:00:00:04:00:03 D ge-0/0/0.10
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC,
B - Blocked MAC)
Ethernet switching table : 2 entries, 2 learned
Routing instance : EVPN-2
Vlan MAC MAC GBP Logical SVLBNH/ Active
name address flags tag interface VENH Index source
v20 50:00:00:03:00:03 DR vtep.32771 198.51.100.1
v20 50:00:00:04:00:03 D ge-0/0/0.20
root@vEX02>
|
MAC アドレステーブルでローカルの ge-0/0/0.10 , 20 にエントリがあること、リモートのエントリが vtep で学習できていることを確認します |
動作確認 - ホスト別コマンドリスト
CSR01 , 02
- ping
- traceroute
- show ip arp
vEX01
- show route protocol ospf
- show route protocol bgp
- show ethernet-switching table
所感
Junos は MX / QFX / EX で共通ですが、EVPN の場合使用できるコマンドにかなり違いがありました。
vJunos-switch は EX9214 模擬ですが、bridge 系は動作しないと見て良いようです。
ネットを調べていると MX の EVPN 設定ガイドが見つかりますが、そのまま使えるコンフィグはほとんど無い印象です。
また Cisco 系では vlan-based が使用可能ですが、Juniper のデフォルトは vlan-aware bundle になるようで、意識してコンフィグできるようになりたいところです。(筆者もわかっているとは言い難い)
今回は Cisco との接続を今後行う可能性を考慮して、vlan-based で設定しました。
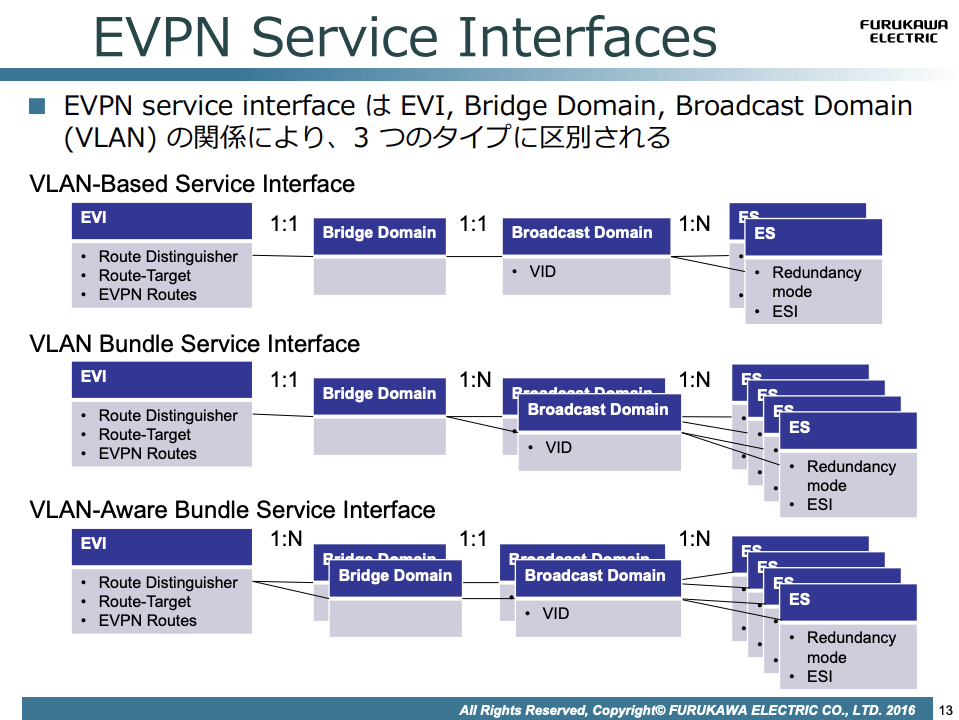
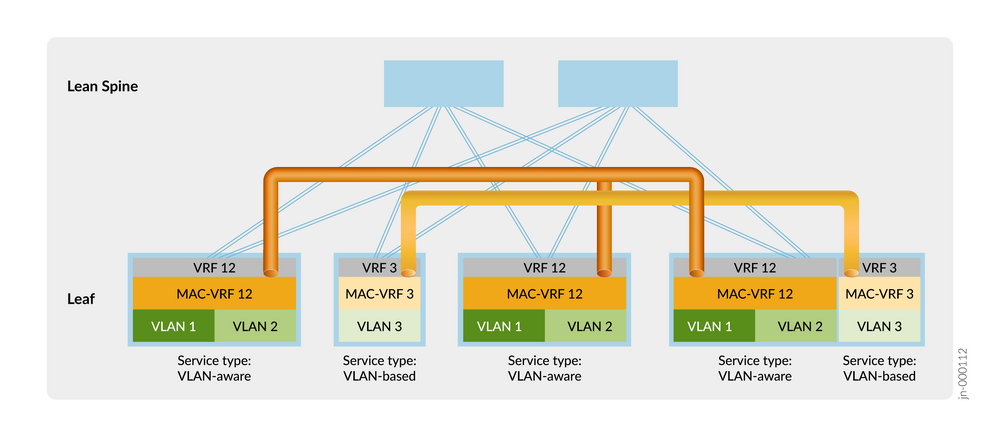
リファレンス
Juniper
Configuring EVPN Routing Instances on EX9200 Switches
日商エレクトロニクス
Juniper QFXで実践! EVPN/VXLANの実力値
JANOG
みんな First-Hop Redundancy どうしてるよ?
EVPN Anycast Gateway を 商⽤導⼊した話
その他
EVPN - VLAN Based と VLAN Aware Bundle の相互接続